Overview
PDFURI tasks us with performing disk forensics and analyzing artifacts with various tools, such as FTK Imager, Event Viewer, PDFStreamDumper, and DB Browser.
Scenario
Our friend “Dee” was looking for a job in Tanta, but it seems she was hacked by one of the malicious websites, so can you examine her hard drive and find some evidence?
Q1
What is the MD5 hash of the malicious document?
Looking around the filesystem we find Application.pdf in the Work user’s Downloads directory.
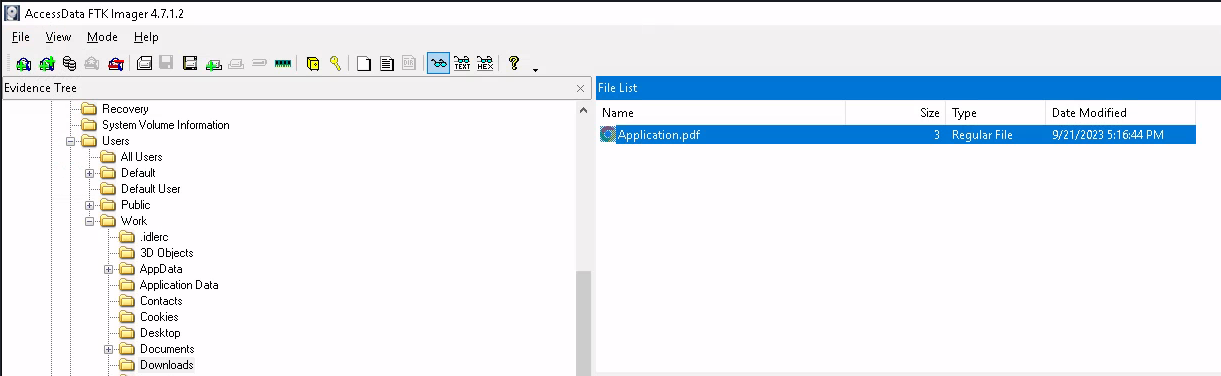
malicious document located in the Downloads directory
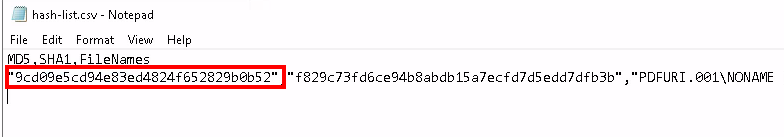
hashes of the malicious document
Answer
9cd09e5cd94e83ed4824f652829b0b52Q2
What is the domain from which the document was downloaded?
In Windows, a user’s browser data is stored in the AppData folder, so we’ll start by looking there. Digging through the directories, we come across Edge. Like Chrome, the history file is located within Edge’s Default directory along with a file called Login Data.
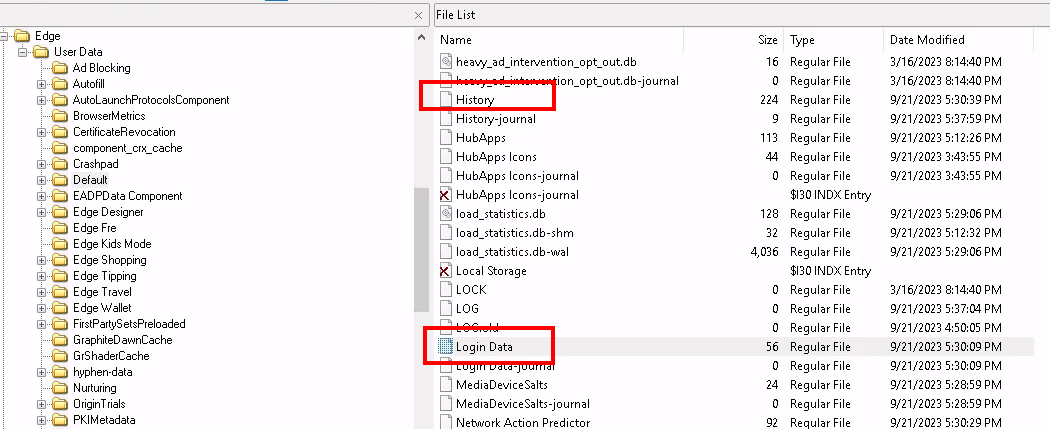
Edge's History and Login Data files
The full path to the Default directory is: C:\Users\Work\AppData\Local\Micorosft\Edge\Default
After exporting the file we’ll view it with DB Browser for SQLite, where we can see the source of the file.
Note: Switch to the “Browse Data” tab and select the “URLs” table.
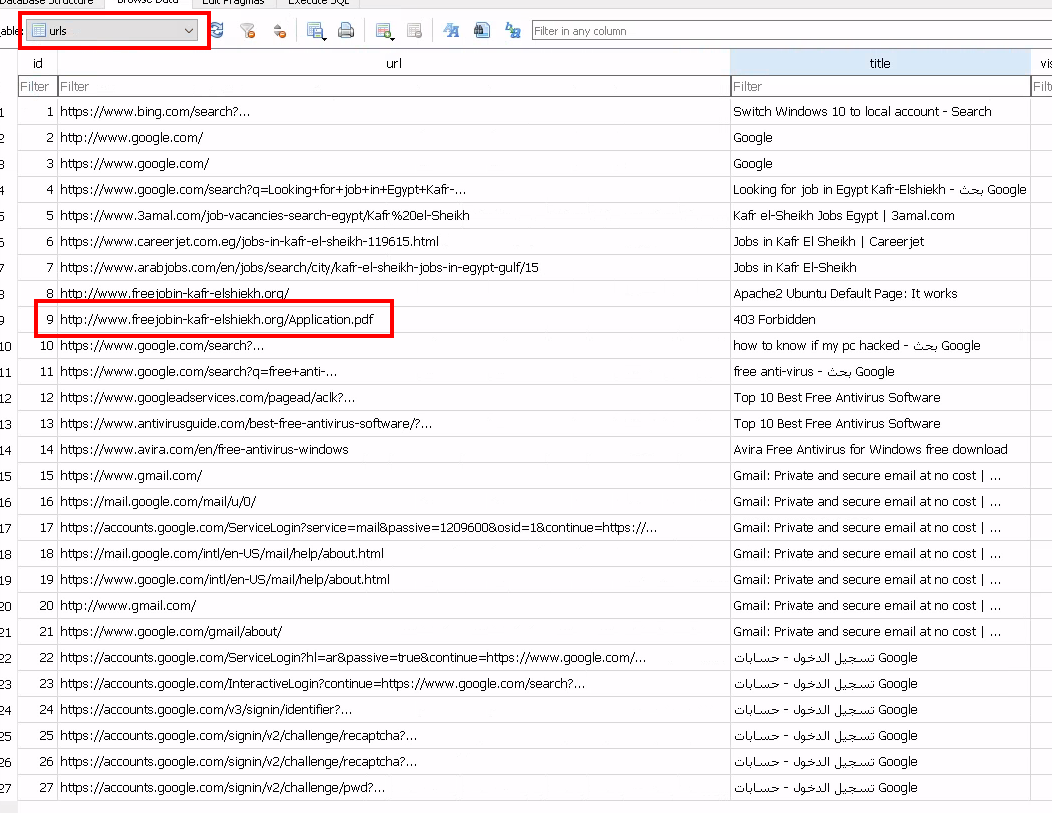
visited URLs as seen in DB Browser for SQLite
Answer
Refang the URL for submission.
hxxp[://]www[.]freejobin-kafr-elshiekh[.]org/Application[.]pdf
Q3
What is the email address of the victim?
We see there was a login to gmail in the browsing history but unfortunately, the account name isn’t present.
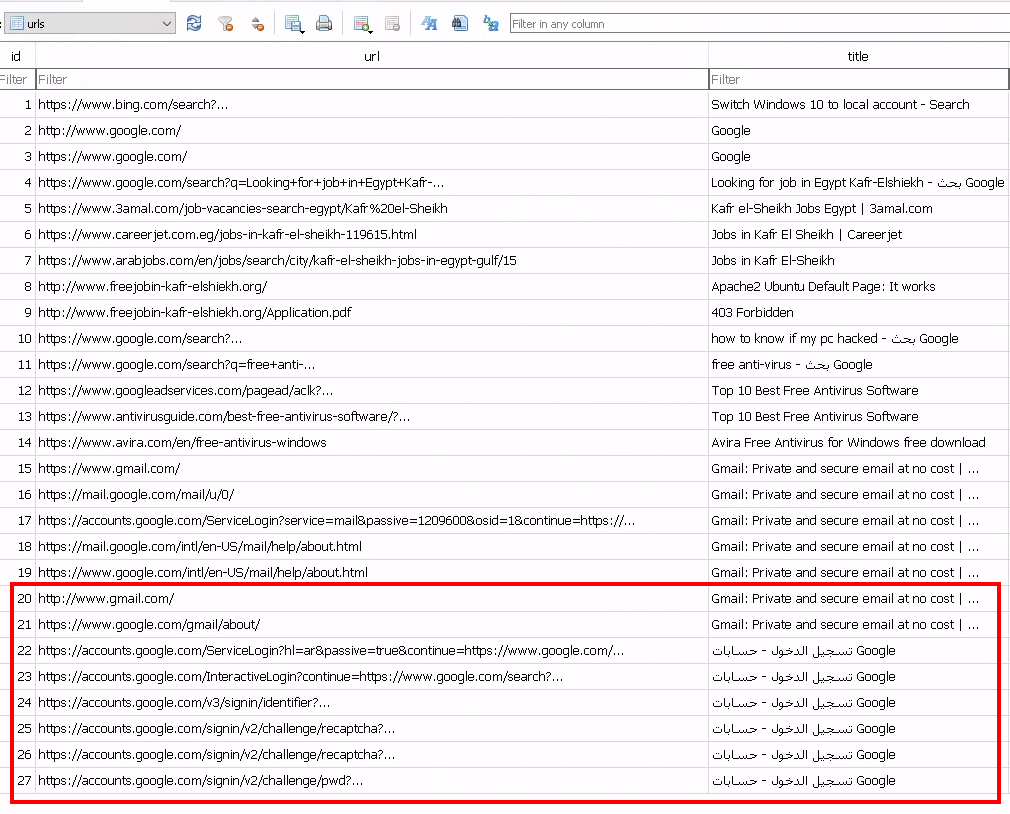
gmail logins
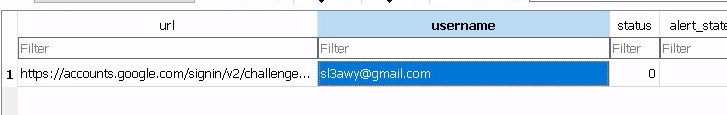
gmail username found in the Login Data file
Answer
sl3awy@gmail.comQ4
What is the command that is executed by the malicious document?
One of the tools provided for this challenge is PDFStreamDumper, so we’ll see what we can find with it. Looking through the results we see obfuscated commands and powershell execution
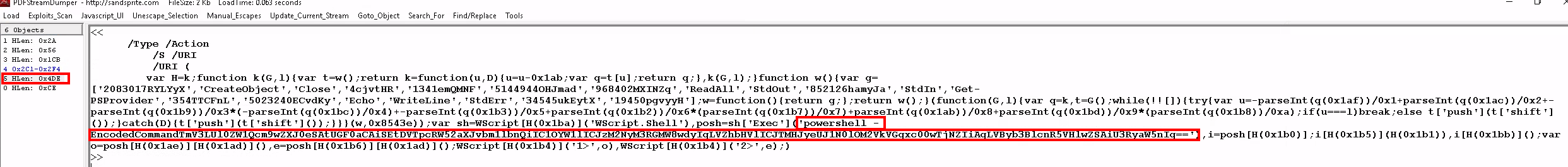
encoded powershell command found in the PDF
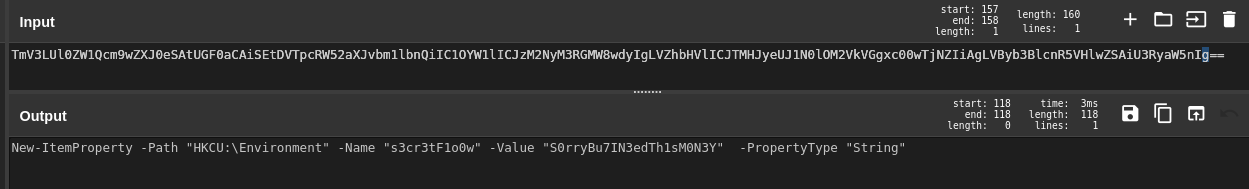
the powershell command decoded
Answer
powershell -EncodedCommand TmV3LUl0ZW1Qcm9wZXJ0eSAtUGF0aCAiSEtDVTpcRW52aXJvbm1lbnQiIC1OYW1lICJzM2NyM3RGMW8wdyIgLVZhbHVlICJTMHJyeUJ1N0lOM2VkVGgxc00wTjNZIiAgLVByb3BlcnR5VHlwZSAiU3RyaW5nIg==Q5
Seems the PC username changed to another one. Can you identify the new Username?
The Windows Security event log captures account changes, so we’ll start our search there.
First, we’ll need to export the Security.evtx file and open it in Event Viewer.
The full path to security.evtx is: C:\Windows\System32\winevt\Logs
Note: To make finding the appropriate logs easier it helps to sort the Logs directory by size since many of the logs are empty.
The Event ID for account changes is 4738, so we’ll filter for that and start looking through the results.
Note: You can read more about Event ID 4738 here: https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=4738
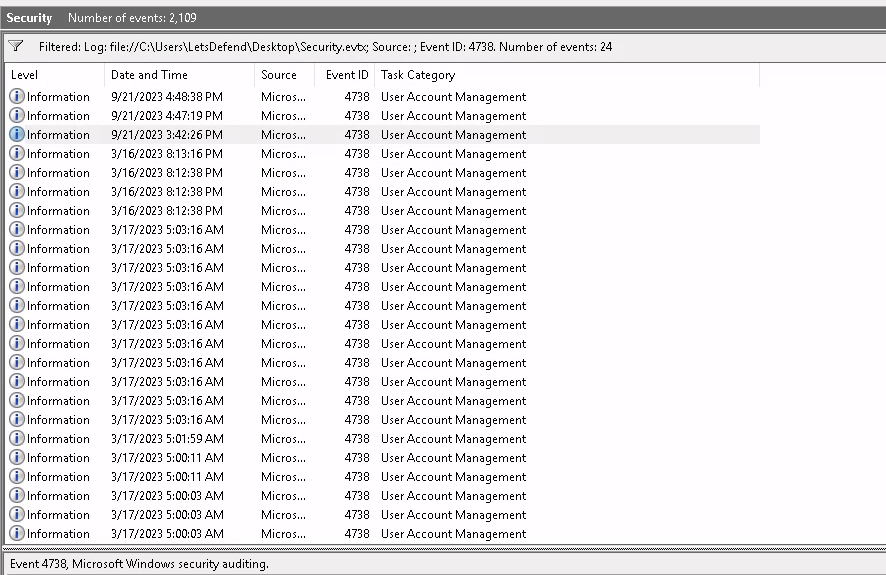
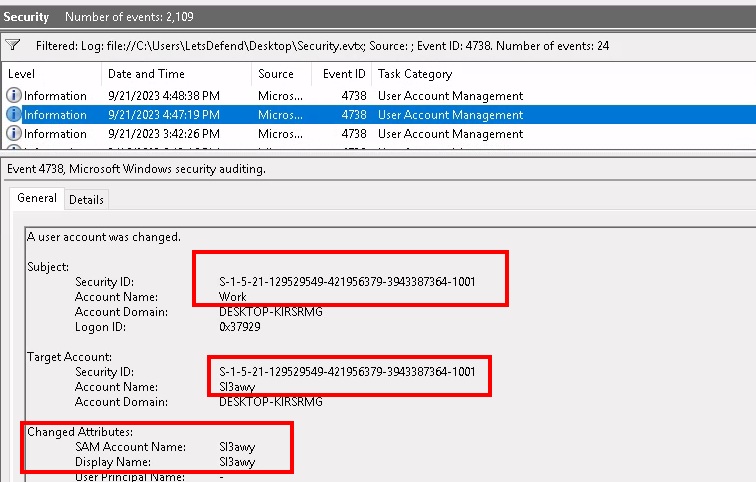
Security.evtx, filtered for Event ID 4738
Looking through the results we can see that the Work account was changed to Sl3awy. We can be sure that this is indeed the same account by observing the TargetAccount’s SID, which matches Work’s.