Overview
For this challenge we’ve been tasked with determining which user downloaded a malicious crack tool, where the file was downloaded, and what actions were taken by the second-stage payload.
Scenario
Our friend fell victim to a suspicious crack tool. But it seems it didn’t go in the right path so investigate it to find any evidence.
Q1
How many users are on the machine?
We can gather a list of usernames by dumping the hashes of the Windows machine.
We’ll use the hashdump command for this. Optionally, we can clean up the output by printing only the Username and RID.
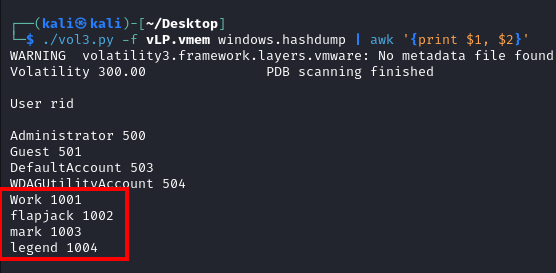
windows.hashdump, filtered with AWK for the first two columns
Note: The command awk ‘{print $1, $2}’ prints the first two columns of hashdump’s output.
Our task is to determine how many user accounts are on the endpoint, RIDs below 1000 are used for services and default Windows accounts. For our purpose, we can ignore those accounts.
Answer
4Q2
Which user is the infected one?
We were told that the victim was exploited by a crack tool, so there must have been a malicious file on the device.
We’ll try searching for files within the Downloads folder to see if there is anything suspicious.
To do this, we’ll use the filescan command and filter it with grep.
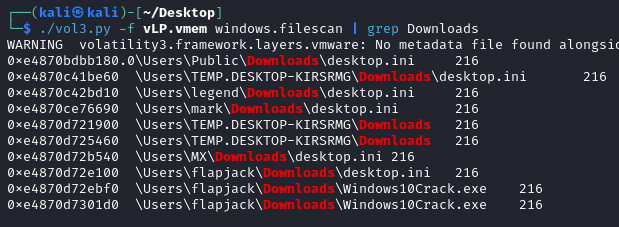
windows.filescan, filtered with grep for strings containing 'Downloads'
Luckily for us, the malicious crack file was located within flapjack’s Download directory so we won’t have to do any more digging.
Answer
flapjackQ3
Which file dropped the ransomware?
We saw the suspicious executable in our results for Q2.
Answer
Windows10Crack.exeQ4
How did that file drop the ransomware [URL]?
To get an idea of what the suspicious file does we’ll need to extract it with windows.dumpfiles.
We’ll need to provide the virtual address of the file. This address was provided in the filescan output we analyzed earlier.
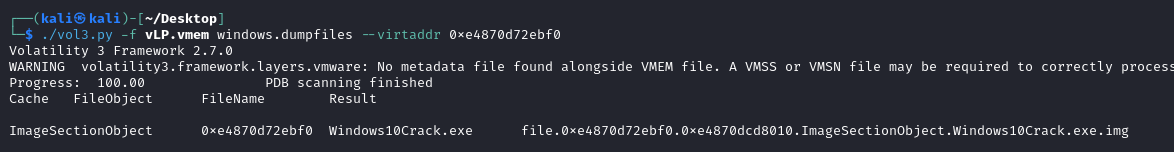
Extracting the suspicious executable with windows.dumpfiles
With the executable extracted, we can start analyzing it for other indicators.
Checking the strings of the file reveals an IP address and a randomly named executable.
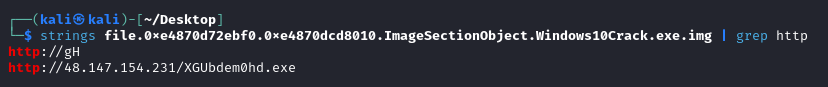
strings of the suspicious crack file, grepped for 'http'
With this information, we’ll need to pivot our investigation to determine if this file was downloaded and what actions it took.
Answer
Refang the URL for submission.
hxxp[://]48[.]147[.]154[.]231/XGUbdem0hd[.]exe
Q5
What is the virtual offset of that ransomware?
We can repeat our filescan search as we did in Q2 but we’ll search for the XGUbdem0hd filename.
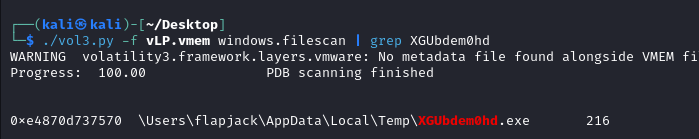
filescan, grepped for the suspicious name
We can see the file is present on the system and located in flapjack’s AppData\Local\Temp\ directory.
Answer
0xe4870d737570Q6
The ransomware edited one of the primary hash manager registry key. Find the key that got modified.
We’ll extract this file, as we did with the crack file, to investigate it further.
Again we’ll use the windows.dumpfiles command and provide it with the virtual address we were given with the filescan output.
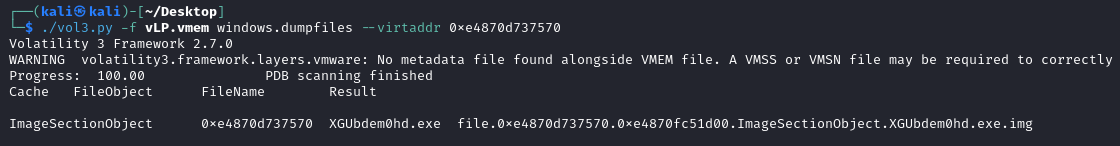
windows.dumpfiles output when dumping the downloaded malware
With the executable available, we can look at its strings and see if we can find any information about what actions it was performing.
We’ve been tasked with determining what registry key it edited, so we’ll start by grepping the contents for the “reg add” command, which is used to add and modify registry keys.
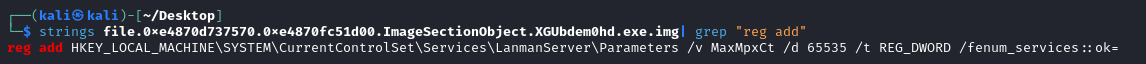
strings, grepped for 'reg add'
We can see that the malware modified the registry value of the LanmanServer\Parameters key.
Alternatively, we can look up the hash of the file on VirusTotal.
We’ll start by grabbing the hash with md5sum.
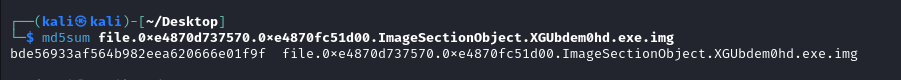
md5 hash of the malware
With the hash in hand, let’s look it up on VirusTotal and see what we find.
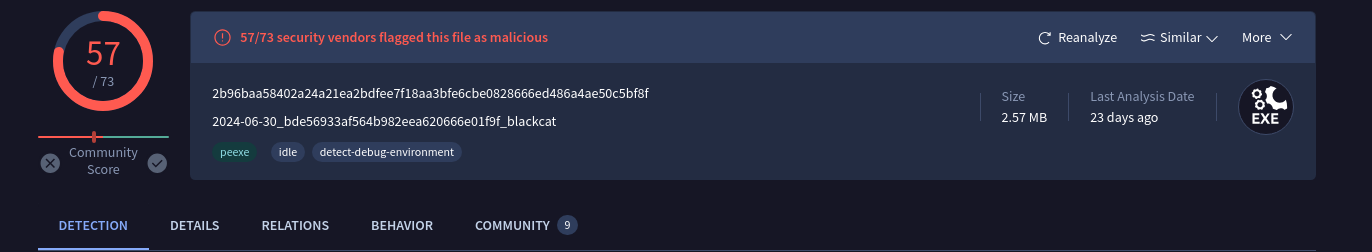
VirusTotal results for the malware
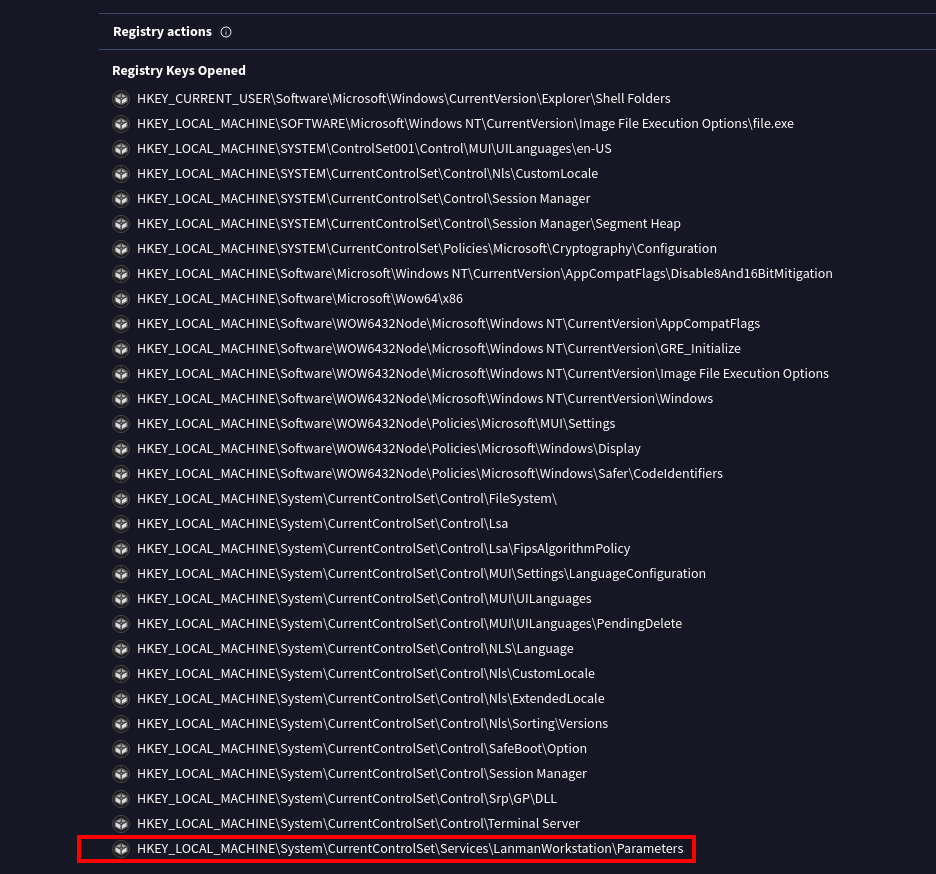
VirusTotal results for the malware
In the Registry Action results on VirusTotal, we can see the key we found within the strings at the bottom of the list.
The list of Registry keys accessed by the executable is much longer in VirusTotal, so this method might require some research if you are unfamiliar with what all of the registry keys represent.
Answer
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanmanWorkstation\ParametersQ7
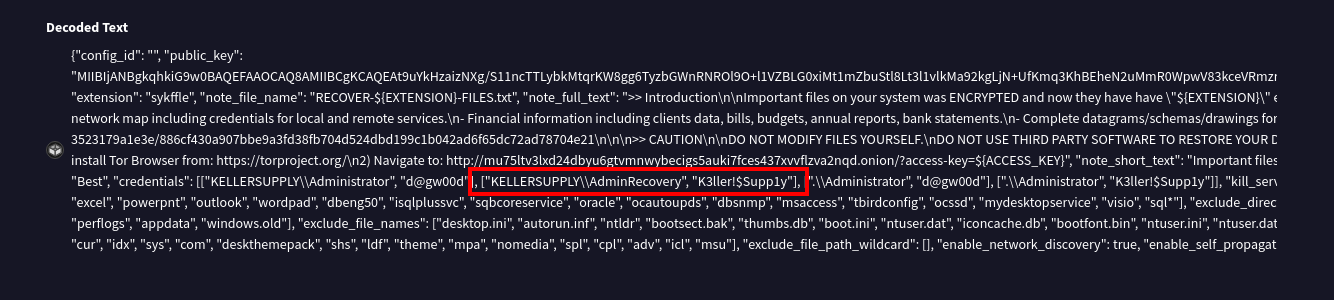
What is the credential of the AdminRecovery?
Again we will check the strings for this entry.

Strings of the malware, grepped for 'Admin'
Our results show a single line with multiple matches for AdminRecovery. Upon closer inspection, we see what appears to be a ransom note and credential pairs.
Similar to Q6, we can also find these results within the VirusTotal results for this file.